Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Manually configure your Azure subscription so that the Client Portal can access your tags and resources.
In some cases, you must configure your Azure subscription manually so that the Client Portal can access the resources and tags.
When you onboard your tenant to the Client Portal, an Enterprise Application called PyraCloud (Azure) is created in your tenant. You must then assign the Tag Contributor and Reader roles to the PyraCloud (Azure) Enterprise Application.
These roles allow the Client Portal to read a list of all the resources in your Azure subscription, and read and write tags on those resources. You can control whether you want the Client Portal to write tags back to resources in your Azure subscription using the Cloud Tenant Setup feature.
Before granting access, ensure that you've onboarded your tenant.
Follow these steps to grant access:
Launch the Azure Portal and search for Subscriptions.
On the Subscriptions page, choose the subscription you want to integrate with the Client Portal.
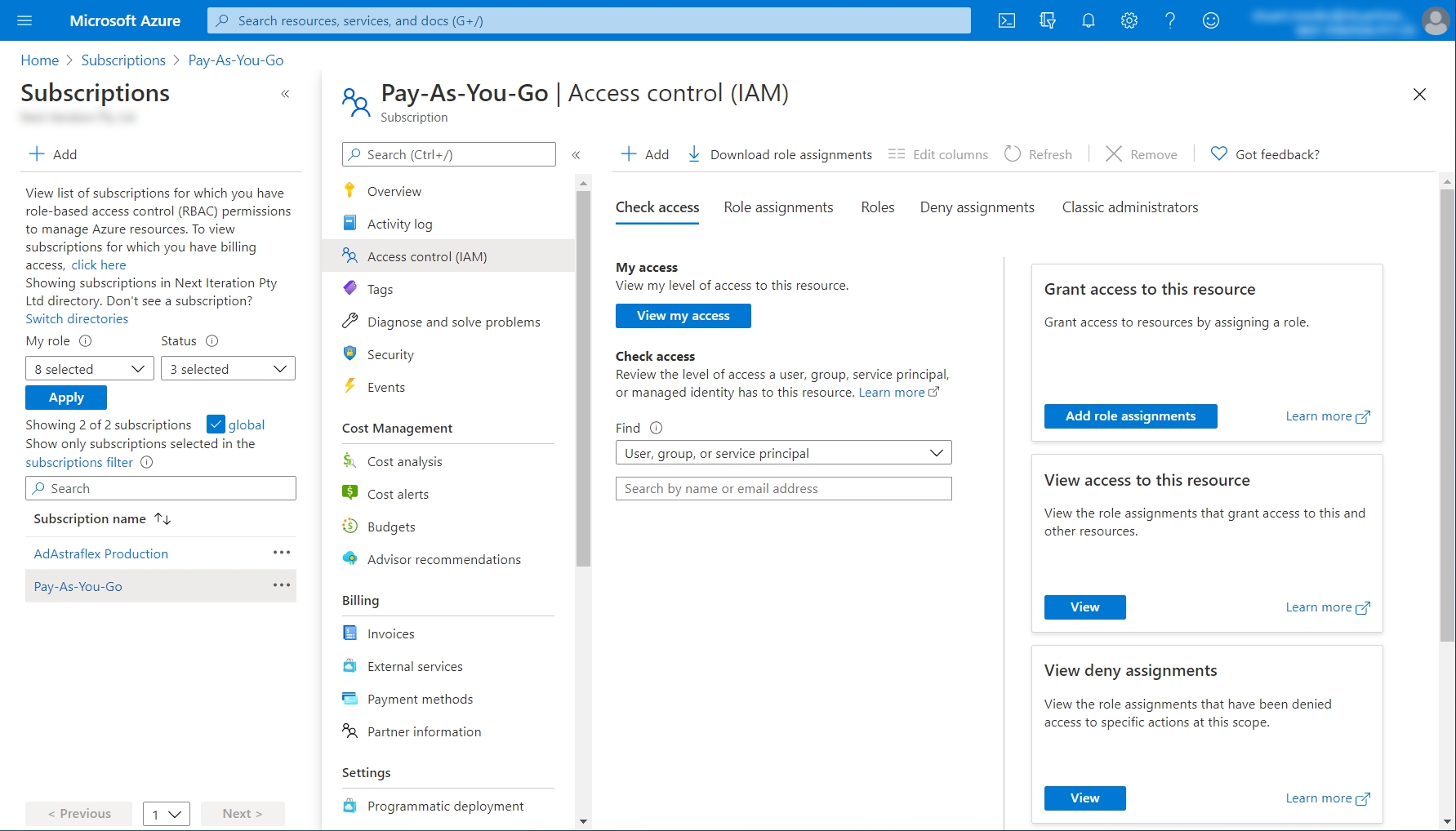
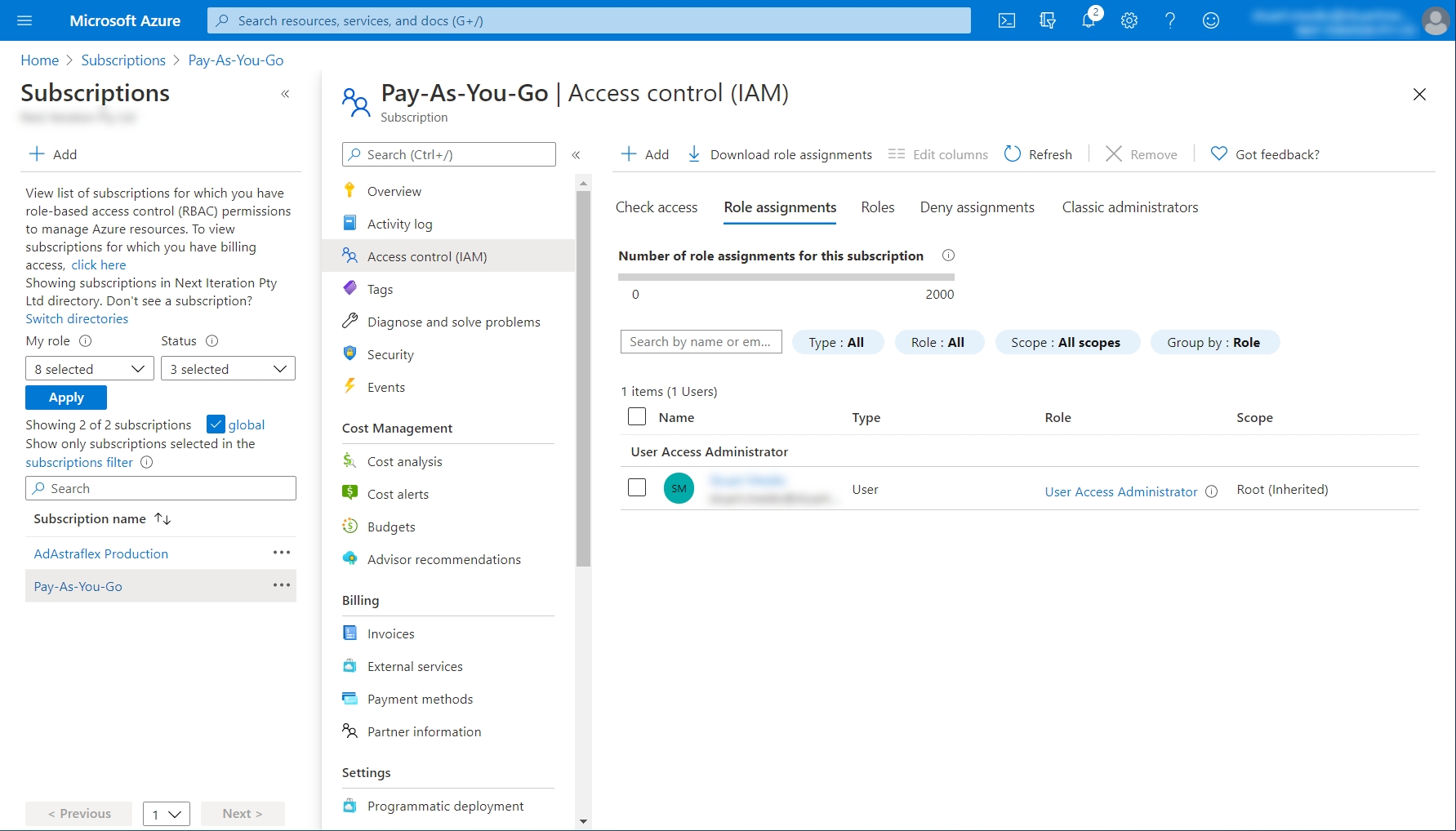
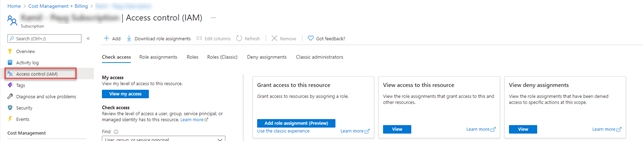
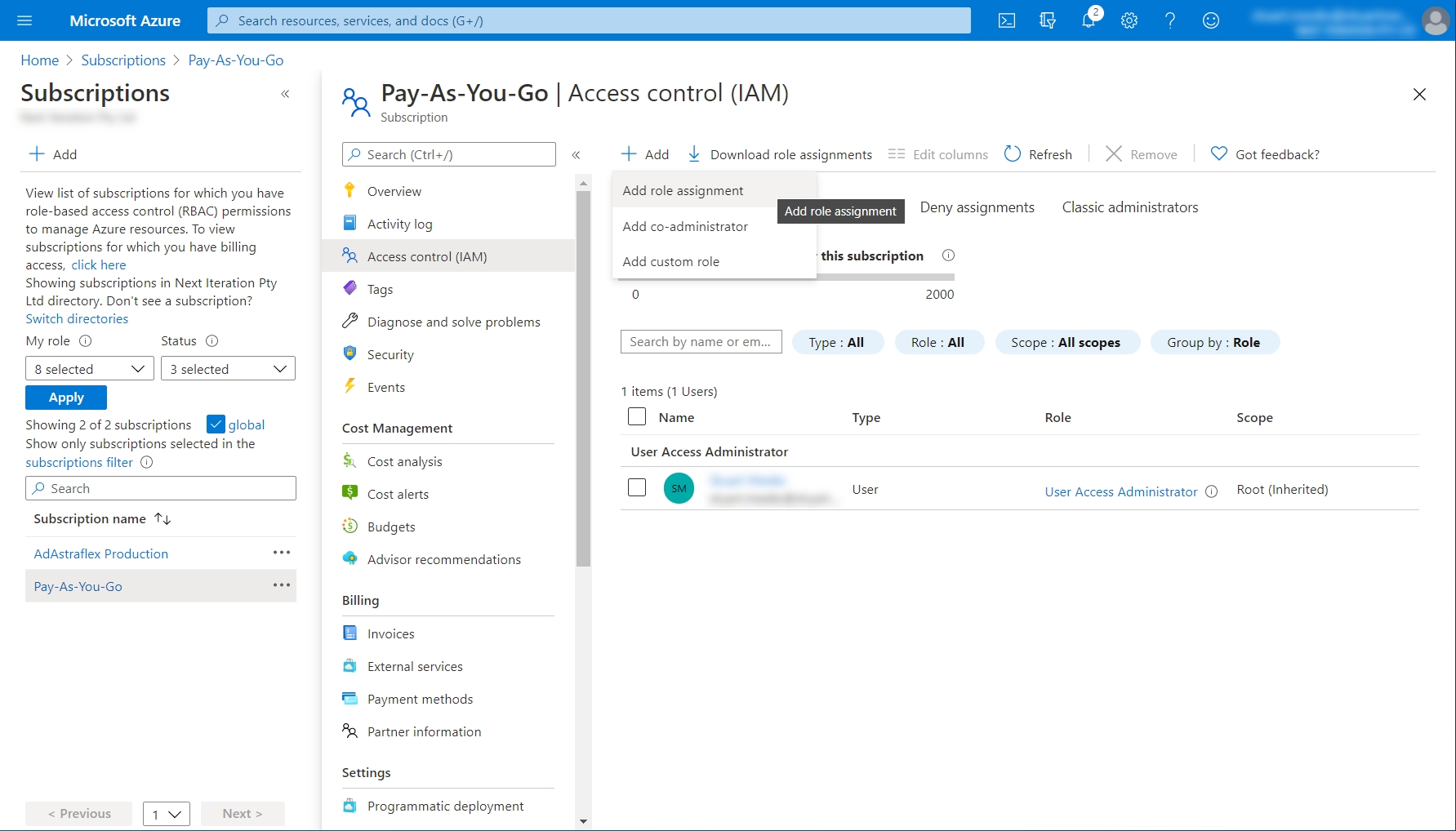
Select Access control (IAM).
Select the Role assignments tab.
Click Add > Add role assignment.
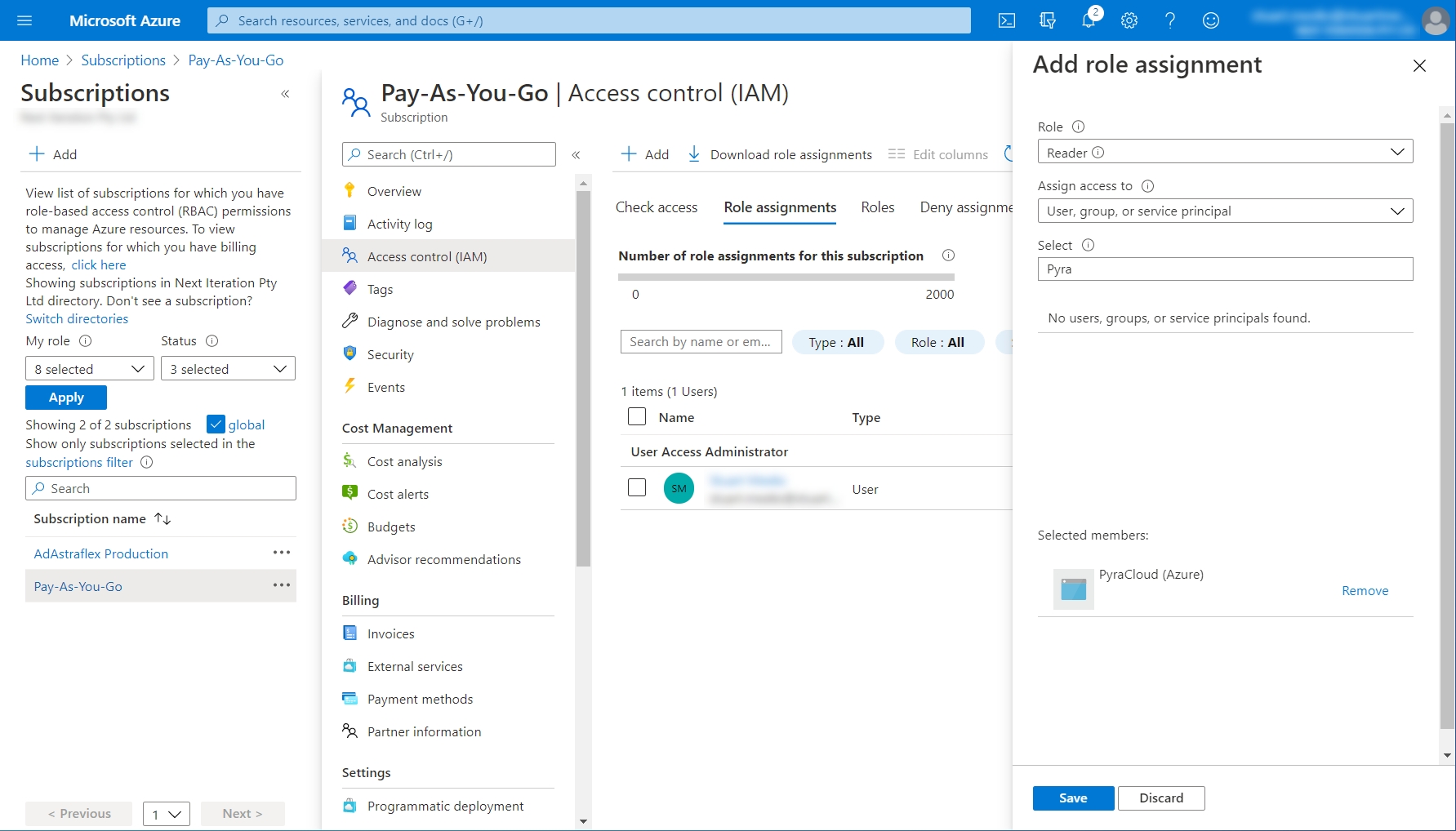
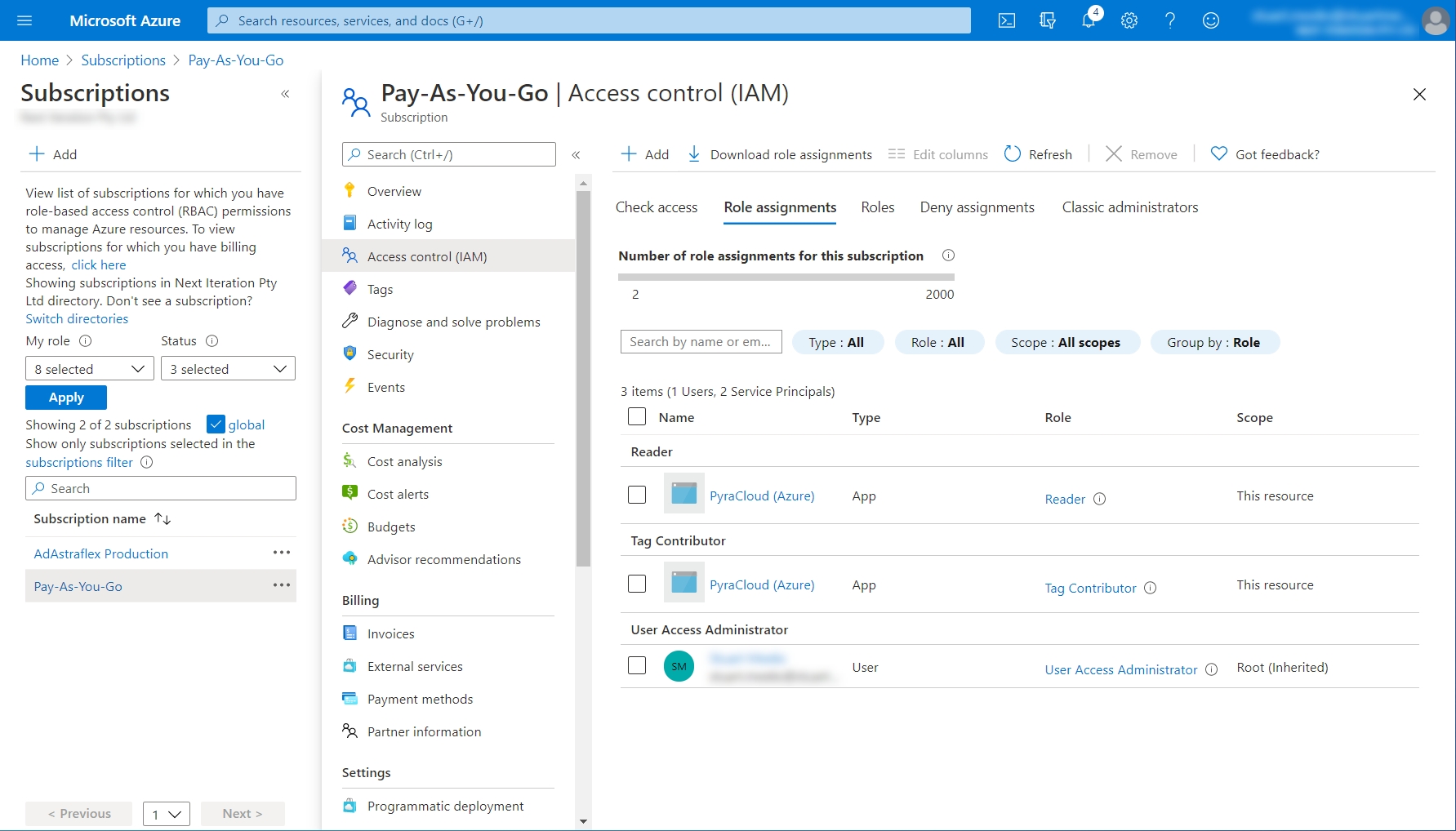
Select Reader from the Role menu and then search for Pyra. Choose PyraCloud (Azure) and click Save.
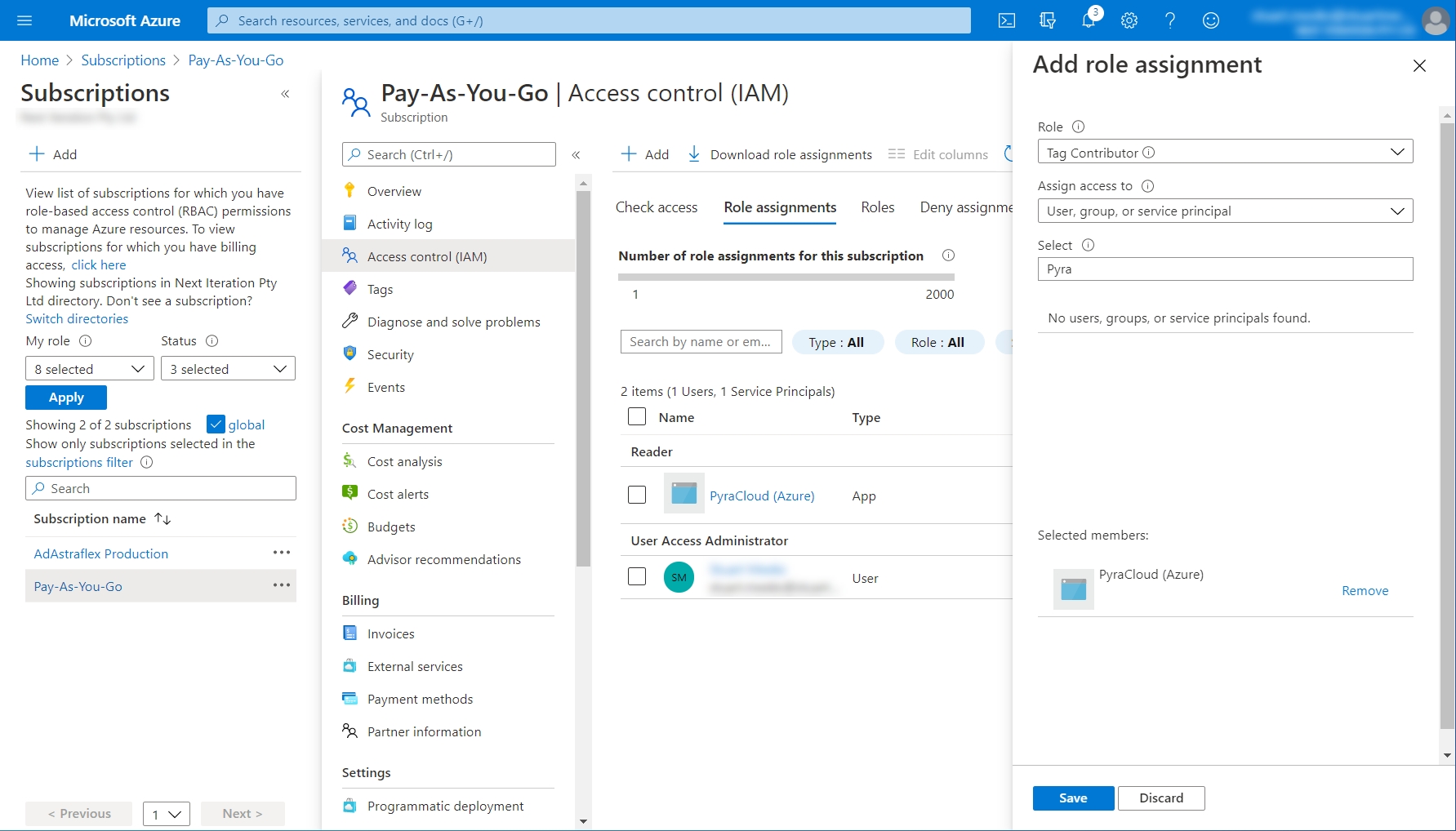
Select Tag Contributor from the Role menu and then search for Pyra. Choose PyraCloud (Azure) and select Save.
The access is granted.
Activate your Microsoft tenant.
If you purchased SoftwareOne's Digital Workplace Essentials/365Simple, and Azure Essentials/ AzureSimple services, you must activate your cloud account in the Marketplace Platform.
Cloud accounts that require activation are displayed on the Cloud tenant setup page and have the Activation Required status and links to activate Microsoft 365 and Microsoft Azure, depending on the service you purchased.
This topic describes how you can access the Cloud tenant setup page and complete the activation.
Follow these steps to activate Microsoft 365:
Navigate to the Cloud tenant setup using one of the following steps:
Click this link: .
Sign in to the platform. Next, open the main menu and go to Cloud tools > Cloud tenant setup.
On the Cloud tenant setup page, locate the account that needs activation. The status will be Activation Required.
In the Actions column, click Activate Microsoft 365.
On the Microsoft sign-in page, enter your username and password. Note that you must provide your Global Administrator credentials.
Review the permissions and click Accept to grant consent.
Follow these steps to activate Microsoft Azure:
Navigate to the Cloud tenant setup using one of the following steps:
Sign in to the platform. Next, open the main menu and go to Cloud tools > Cloud tenant setup.
On the Cloud tenant setup page, locate the account that needs activation. The status will be Activation Required.
In the Actions column, click Activate Microsoft Azure.
On the Microsoft sign-in page, enter your username and password. Note that you must have the Owner or User Access Administrator role for the account to activate.
Review permissions and click Accept to grant consent.
On successful validation of your credentials, your account is activated and the Cloud tenant setup page displays the activation status as Connected.
Manually integrate your Azure tenant and assign the Reader and Tag Contributor roles.
You can integrate your Microsoft tenant with the Client Portal using the following steps:
Grant consent to the Client Portal in your Azure tenant.
Assign the and access roles to the Client Portal using Azure Management Groups.
Share the details with SoftwareOne to complete your onboarding.
The Tag Contributor and Reader roles allow the Client Portal to read a list of all the resources in your Azure subscription, and read and write tags on those resources. You can control whether you want the Client Portal to write tags back to resources in your Azure subscription. For more information, see .
Follow these steps to grant consent through your Azure tenant:
Select one of the following links:
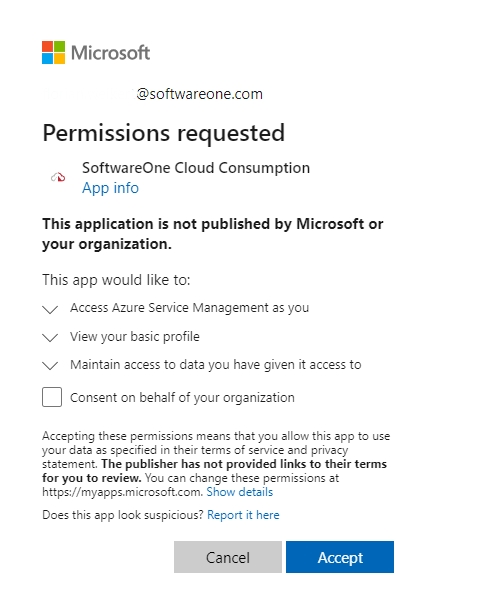
On the Permissions Requested page, review the permissions, and select Accept.
After granting consent, launch the Azure Portal and navigate to Azure Active Directory > Enterprise applications to make sure that the Client Portal/PyraCloud is listed in your enterprise applications.
Follow these steps to assign the Tag Contributor and Reader access roles:
Launch the and search for Management groups.
On the Management groups page, select Start using management groups.
Provide the Group ID and a display name for your group. Select Submit. The new group will be created and displayed under the Tenant Root Group.
Select the newly created management group and then from the left sidebar, select Access Control (IAM).
Navigate to Role assignments and select Add > Add role assignment from the dropdown.
Assign the Reader role to the Client Portal:
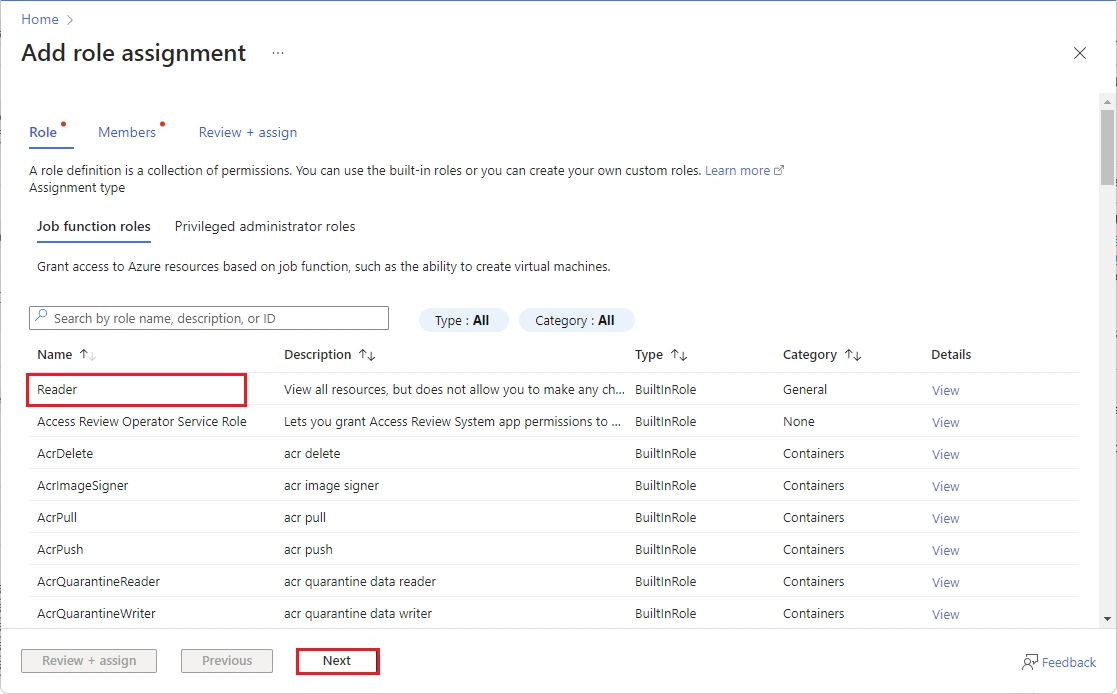
Choose Reader from the list of roles and select Next.
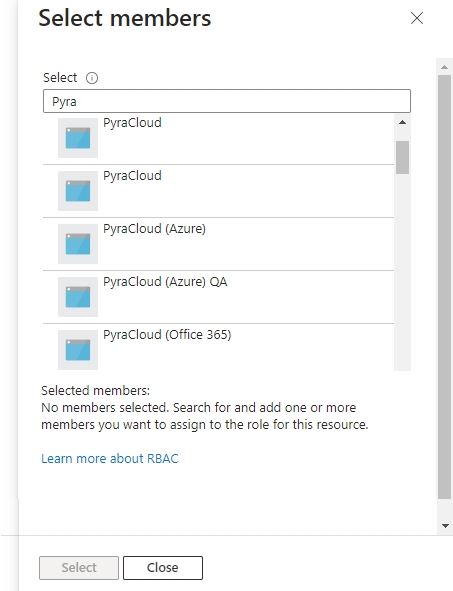
On the Members tab, click Select Members, and then in the Search box, type PyraCloud.
From the search results, choose PyraCloud (Azure) for Azure or PyraCloud (Office 365) for Office 365. Select Save.
Assign the Tag Contributor role to the Client Portal:
Choose Tag Contributor from the list of roles. Select Next.
On the Members tab, click on Select Members, and then in the Search box, type PyraCloud.
From the search results, choose PyraCloud (Azure) for Azure or PyraCloud (Office 365) for Office 365. Select Save.
Select Review + assign and then Review + assign again. The new roles will be displayed on the page.
After you’ve completed the integration steps, provide the following details so that we can complete the onboarding of your tenant:
Your Microsoft Tenant ID (or domain).
A friendly name for your tenant to recognize easily across the Client Portal.
The start and end date of your Enterprise Agreement.
After we’ve added your tenant, you will also need to provide an access token from the EA Portal. For information on how to provide an access token, see Add an Access Token.
Add your EA or MPSA cloud account to the Client Portal.
Before adding an account, make sure that you have the following details:
Account Information - You must have the tenant ID or domain name of the tenant that contains your Azure or Office 365 subscriptions. The tenant ID and domain name are available in your Azure account. For information on how to find these details, see in the Microsoft documentation.
Permissions - You must have sufficient permissions to complete the onboarding process. The setup will fail if the permissions are not configured in the .
For an Azure account, you must have owner permission for the subscription you want to add.
For an Office 365 account, you must be a Global Administrator of the tenant that contains the subscriptions.
Follow these steps to add a new cloud account to the Client Portal:
Navigate to the page and click Add Cloud Account.
On the Add Cloud Account page, click Azure and provide the following details:
Friendly Name - Provide a name for your Microsoft tenant.
Microsoft Tenant ID or Tenant Domain - Provide the tenant ID or domain.
License Model - Select the license model (Enterprise Agreement or Microsoft Customer Agreement).
Enrollment Number - Provide the enrollment number. Note that this field is displayed only if you select Enterprise Agreement as your license model.
Click Add Cloud Account.
Sign in to the Microsoft portal using the credentials of a user who has Owner permissions to the Azure subscriptions you want to add.
On the consent page, review the permissions required by the Client Portal and click Accept to grant consent.
After clicking Accept, you'll be redirected to the Cloud Tenant Setup details page to view the new tenant and its activation progress. After activating your tenant, you can add subscriptions and allow the Client Portal to write tags back to your Azure resources.
Many organizations have several Azure subscriptions in a single Microsoft tenant. In some cases, it's not always the same person who has Owner permissions on all those subscriptions. In such cases, each subscription owner must activate their own subscriptions.
Follow these steps to add more subscriptions:
On the Cloud Tenant Setup page, click Manage and then select Add Existing Subscriptions to add more subscriptions.
In Add New Subscription, select the type of subscription and click Add.
If you select Azure, the user performing consent must be the Owner of the Azure subscriptions being added.
If you select Office 365, the user performing the consent must be a Global Administrator of the tenant.
Sign in to the Microsoft portal using the credentials of the user with Owner permissions to the Azure subscriptions you want to add.
On the consent page, review the permissions and click Accept to grant consent. After granting consent, you'll be redirected to the Client Portal.
When you activate your Azure subscriptions for the first time, the Client Portal assigns the Reader role by default. This means that the Tags and Resources feature can import your resources and tags from Azure, but it cannot synchronize any tag changes you make in the Client Portal back to Azure.
For Tags and Resources to synchronize tags back to Azure, you must change the level of access the Client Portal has for your Azure subscription.
Follow these steps to change the level of access:
On the Cloud Tenant Setup page, click Manage.
Click Change Access for the subscription you want to modify.
Select one of the following access levels and click Change:
Sync resources only, no tags – write back of tags disabled - Tags and Resources will download your resources to the Client Portal without the tags currently assigned in Azure. Any changes to tags will be stored in the Client Portal only. This setting requires the “Reader” role in your Azure subscription and will not make any changes to resources or tags in your Azure subscription.
Sync resources and tags – write back of tags disabled - Tags and Resources will download your resources, including the tags currently assigned in Azure. Any changes to tags will be stored in the Client Portal only. Any tags assigned to resources in Azure will overwrite the tags for the corresponding resource in the Client Portal. This setting requires the Reader role in your Azure subscription and will not make any changes to resources or tags in your Azure subscription.
Sync resources and tags – write back of tags enabled - Tags and Resources will download your resources to the Client Portal including the tags currently assigned in Azure. Any changes to tags will be synchronized back to your resources in Azure. This setting requires the “Tag Contributor” role in your Azure subscription and will only make changes to tags.
Sign in to the Microsoft portal using the credentials of the user with Owner permissions to the Azure subscriptions for which you wish to modify the access level.
On the consent page, review the permissions and click Accept to grant consent. After granting consent, you'll be redirected to the Client Portal to view the updated access level. If you notice a blank screen, refresh the page.
Add your Azure Microsoft Customer Agreement account to the Client Portal.
The Client Portal supports both legacy Enterprise Agreement and modern models. If you are adding an EA or MPSA account, see .
Before adding an account, note the following points:
Make sure you've followed the steps in .
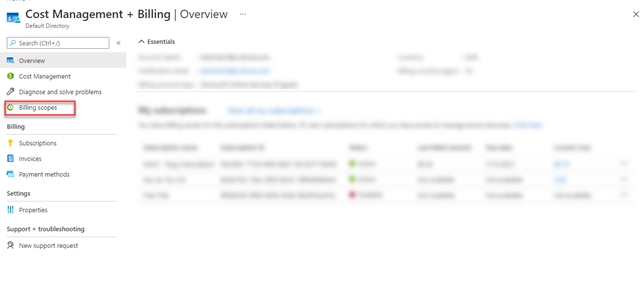
Make sure your account has the proper billing account type set up. To verify this, launch the . From the left navigation pane, select Cost Management + Billing. Then, navigate to Settings > Properties. The account type is displayed in the right pane.
Follow these steps to assign the Billing account reader role to the Client Portal:
Sign in to the and search for Cost Management + Billing.
In the left navigation pane, select Billing scopes and then select your MCA billing scope.
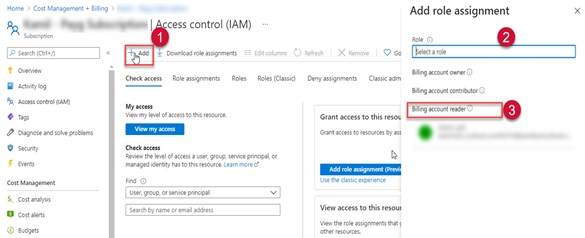
Select Access Control (IAM) to assign permissions.
Select Add and then from the Role dropdown list, select Billing account reader.
Select the PyraCloud (Azure) application.
Select Save. Your MCA billing data will be synchronized with the Client Portal after 24 hours.
Click this link: .
If you wish to add more Azure subscriptions owned by other users, you can do this later. For instructions, see .
When you return to the Client Portal, you might see a blank page for a few seconds. To learn about the process that takes place after you provide consent, see
Use Azure Management Group to assign permissions across multiple subscriptions in a single step.
You can use Azure Management Groups to grant the Client Portal access to your Azure subscriptions. This approach has the following benefits:
You can assign access to multiple subscriptions in a single step.
If you create more Azure subscriptions in the future, access will be automatically granted. It means when you add an Azure subscription to your tenant, activating it in the Client Portal is unnecessary.
Before granting access using Azure CLI, note the following points:
Ensure that you've installed PowerShell and Azure CLI. For installation instructions, see Install PowerShell and Install Azure CLI.
The script utilizes PowerShell variables, therefore, you must execute this script at a PowerShell prompt instead of a normal command prompt.
Use the following commands to onboard your Azure subscriptions:
The following table explains these commands:
az login
Log in to your Microsoft tenant.
az rest --method post --url "/providers/Microsoft.Authorization/elevateAccess?api-version=2016-07-01"
az ad sp create --id 2a4807a4-d9e4-457d-b32f-a455e0d3662a
az ad app permission grant --id 2a4807a4-d9e4-457d-b32f-a455e0d3662a --api 00000003-0000-0000-c000-000000000000 --scope "User.Read"
Create the PyraCloud (Azure) service principal (Enterprise Application) in your tenant.
$root_mg=$(az account management-group list --query "[?displayName == 'Tenant Root Group'] | [0] | id" --output tsv)
Get the ID of your Tenant Root Group.
az role assignment create --assignee "2a4807a4-d9e4-457d-b32f-a455e0d3662a" --role "Reader" --scope "$root_mg"
az role assignment create --assignee "2a4807a4-d9e4-457d-b32f-a455e0d3662a" --role "Tag Contributor" --scope "$root_mg"
Assign the Reader and Tag Contributor roles to the PyraCloud (Azure) application in your Tenant Root Group.
Before granting access through the Azure Portal, note the following points:
Ensure that you've onboarded your tenant.
Ensure that have the correct permissions to manage access to all Azure subscriptions and management groups in your tenant. For instructions, see Elevate access to manage all Azure subscriptions and management groups in the Microsoft documentation.
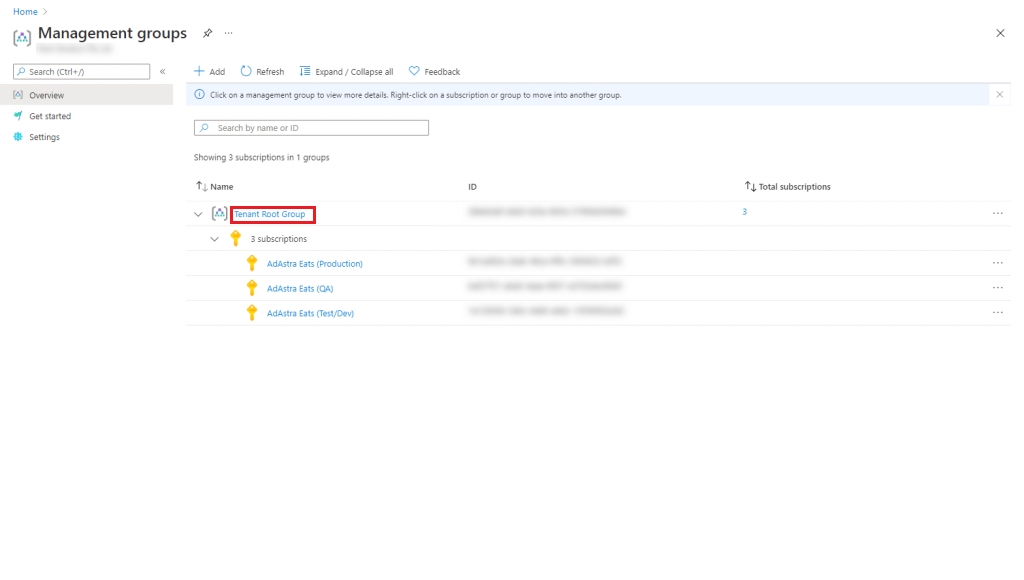
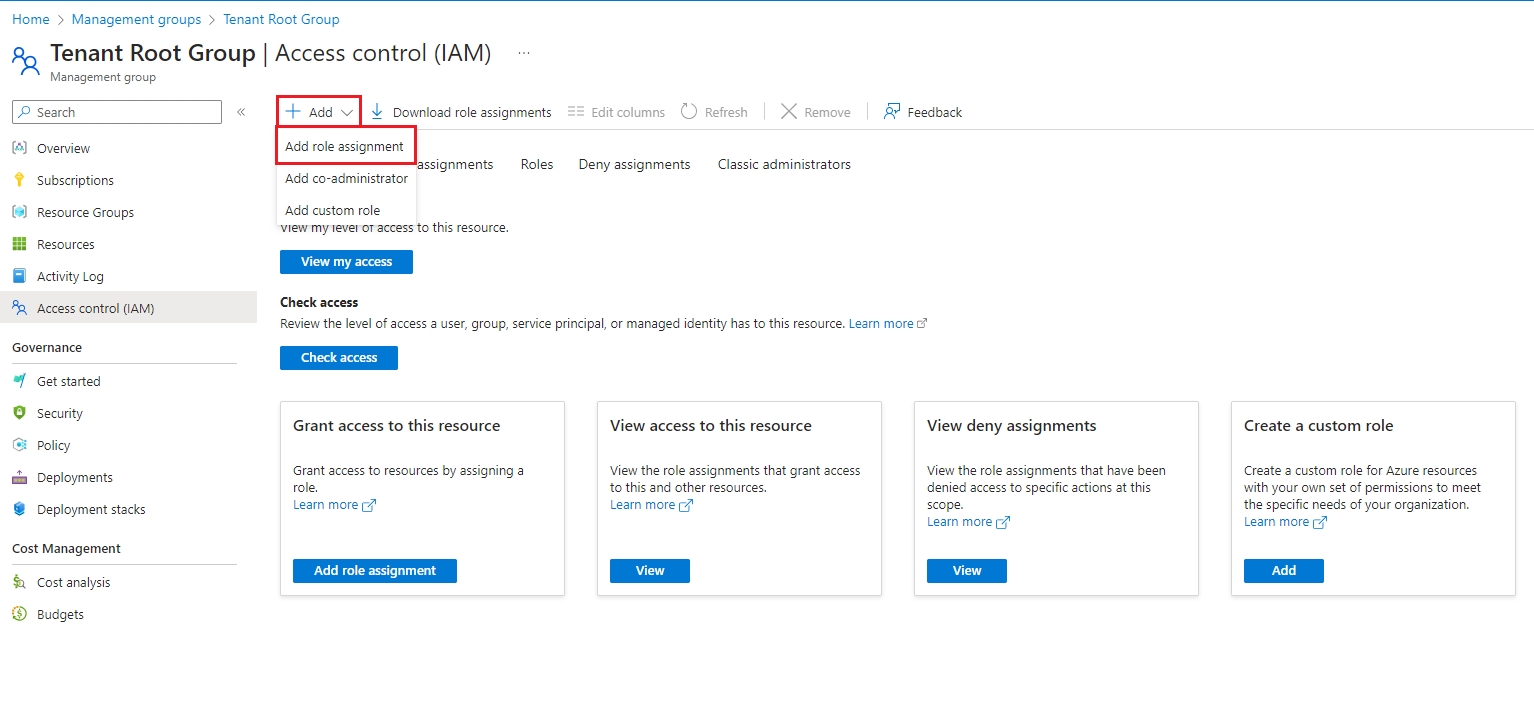
Launch the Azure Portal and search for Management groups.
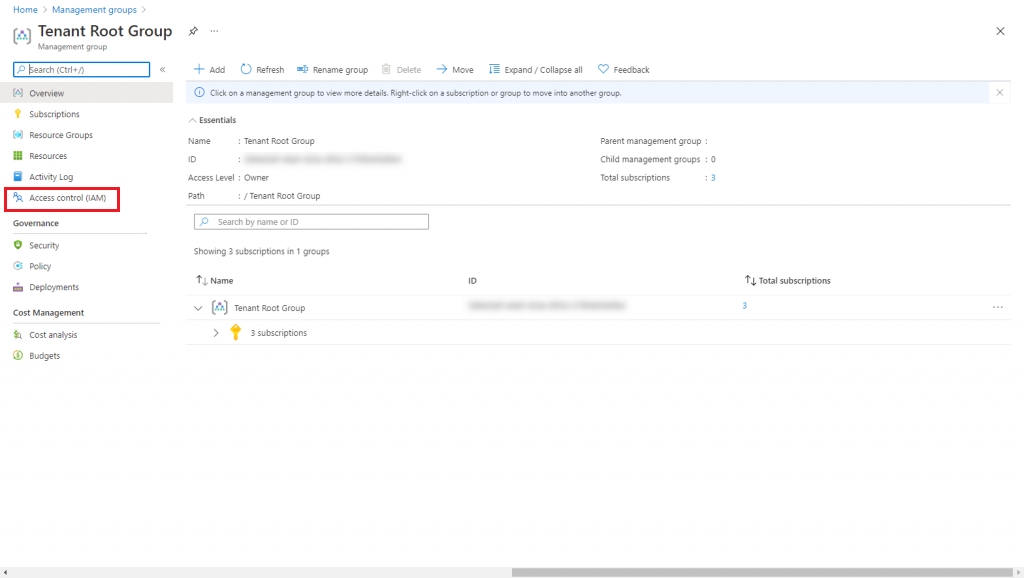
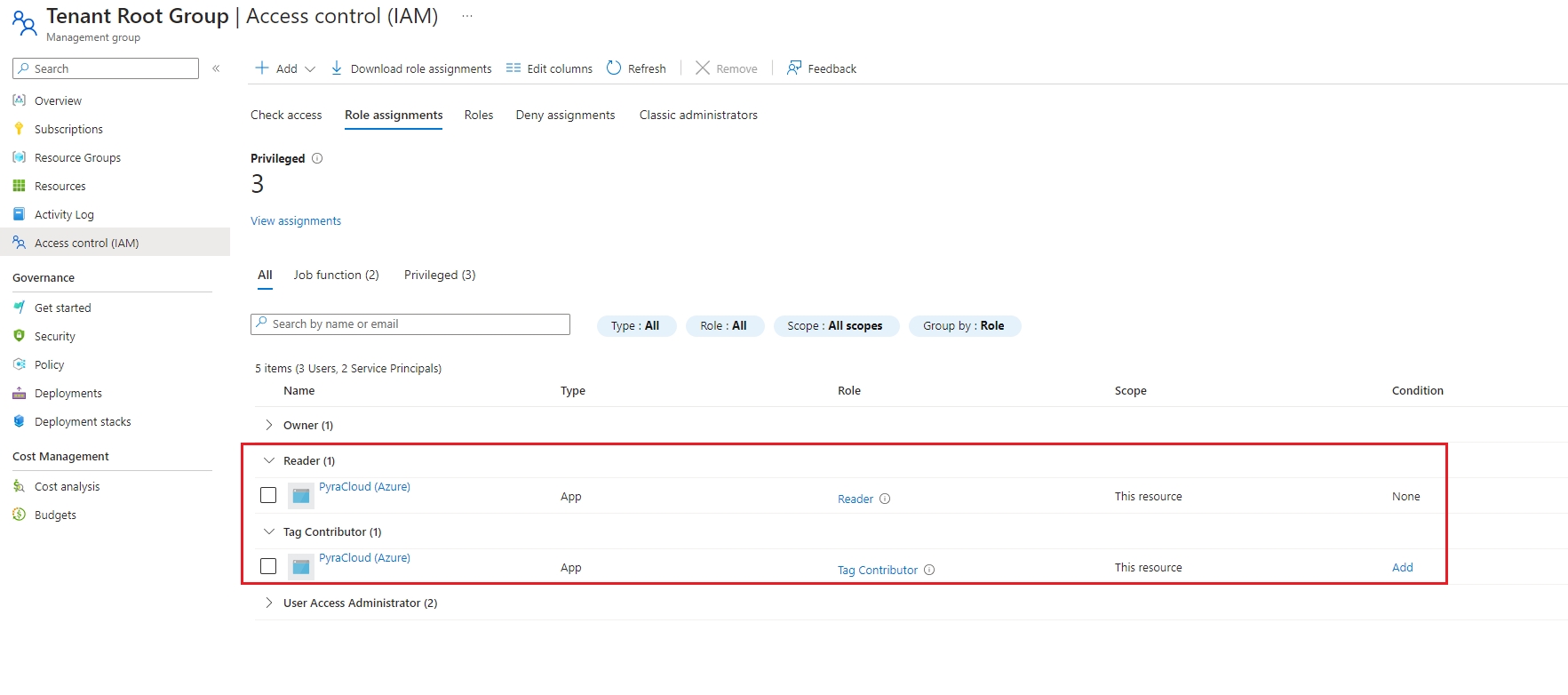
On the Management groups page, select Tenant Root Group. Note that regardless of your organization's configuration, you'll always have a Tenant Root Group. It might have been renamed, but it always appears at the top of the hierarchy.
From the left sidebar, select Access control (IAM).
Click Add > Add role assignment.
The Add role assignment page opens.
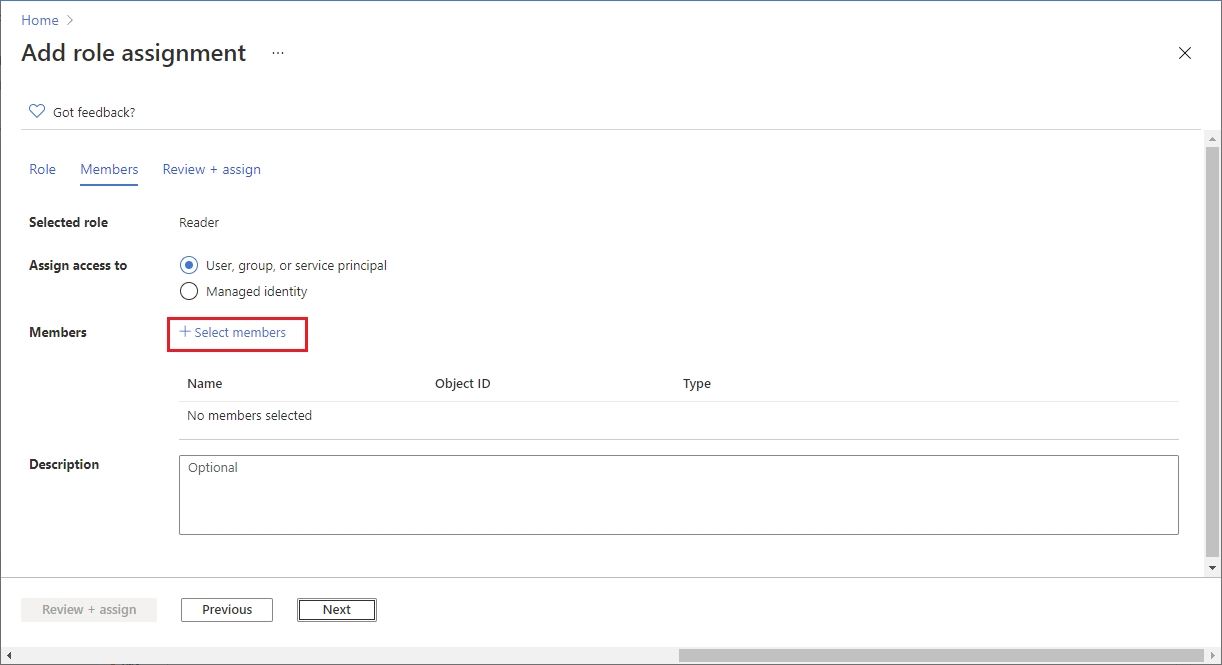
On the Role tab, select Reader as the role and click Next. The Member tab opens.
Select User, group, or service principal if it's not selected by default, and then click Select members.
In the Select members panel, type Pyra and then select PyraCloud (Azure) from the search results.
Click Select to add PyraCloud (Azure) to the Members list. Once PyraCloud (Azure) is added, click Review + assign.
On the Review + assign tab, review the details and click Review + assign to confirm the role assignment.
To assign the Tag Contributor role, follow all of the steps in Step 3: Assign the Reader role, but choose Tag Contributor as your role instead of Reader.
After you've completed the steps, the roles are assigned and displayed on the Role assignments tab.
Migrate from Azure Enterprise Reporting to Cost Management APIs.
Microsoft will retire the legacy Azure Enterprise Reporting APIs on 1 May 2024. Currently, the Client Portal uses these APIs to get your Azure EA consumption data.
If you have an Azure Enterprise Agreement (EA), you must migrate to the new Azure Cost Management APIs to maintain your cost and usage data in the Client Portal.
Before migrating to the new Cost Management APIs, note the following points:
The new APIs don't require access tokens because the authorization is done through Microsoft Entra ID (also known as Azure Active Directory) using service principals.
Only individuals with the Azure EA Enterprise Administrator role permission can carry out the migration steps. If you have trouble finding out who is your EA admin in Azure, see Microsoft's documentation on EA Billing administration on the Azure portal.
During the consent flow, the SoftwareOne Cloud Consumption app is added to the organization tenant. This enterprise application is granted the EA Reader permission, which allows us to read the consumption data. To add the application to the tenant, you'll need permission to approve an Enterprise Application.
If your EA admin doesn't have access to the Client Portal, you can collaborate with them by sharing your screen, so your EA admin can sign in and complete the authorization required for migration.
During migration, our system automatically assigns the EnrollmentReader role permission to the service principal.
If you've already onboarded your EA cloud account to the Client Portal and have appropriate permissions to approve Enterprise Applications, follow these steps to transition to the new API:
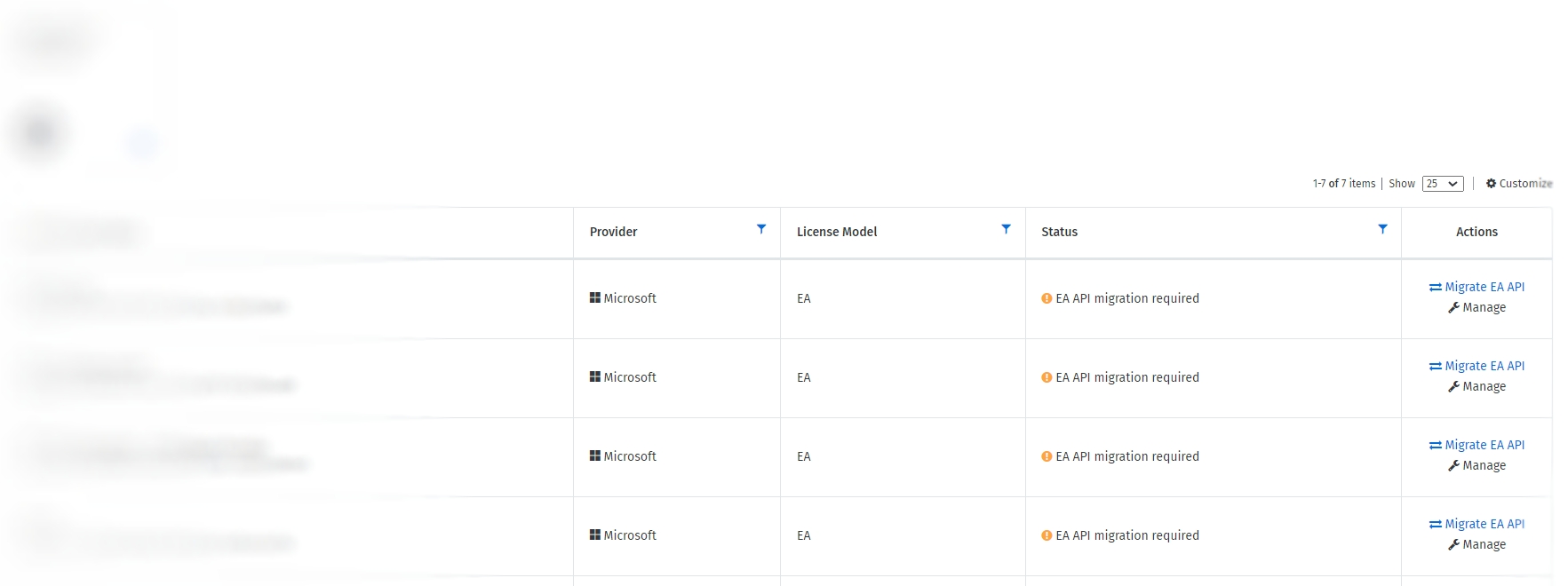
Open the Cloud Tenant Setup page. EA cloud accounts that haven't been migrated will display EA API migration required in the Status column.
Click Migrate EA API.
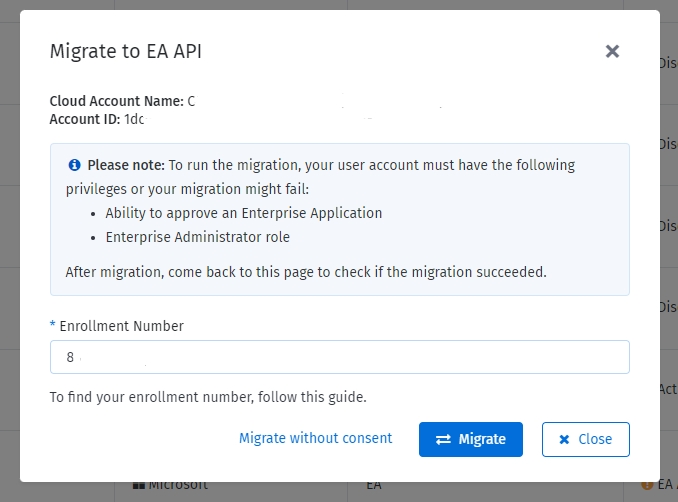
In the Migrate to EA API window, enter the enrollment number and click Migrate.
Sign in to the Microsoft portal using the credentials of a user with Enterprise administrator permission.
On the consent page, review the permissions required by the Client Portal and click Accept to grant consent.
After clicking Accept, you'll be redirected to the Cloud Tenant Setup details page.
The system will mark the enrollment number you provided as migrated, and automatically assign the Enrollment reader permission to the PyraCloud (Azure) application. When the migration is completed, the consumption data is fetched from Microsoft.
Migration did not complete successfully?
If the migration fails despite following these steps, you can use the fallback option to complete the process.
To do so, go to the Enrollment Numbers tab of the tenant and click Show manual steps in the Actions column. When the Manual steps dialog opens, execute the commands and then click Close.
If you are still unable to migrate, contact your support team.
If you cannot provide consent to approve enterprise applications or have environment restrictions, you can follow these steps to migrate and assign permissions manually:
On the Cloud Tenant Setup page, locate the required EA cloud account with the status EA API Migration required.
In the Actions column, click Migrate EA API.
In the Migrate to EA API window, enter the enrollment number and click Migrate without consent.
On the details page of the tenant, select the Enrollment Numbers tab and click Show manual steps.
In Manual steps, assign permissions using Cloud Shell or REST API and click Close. Note that you must have the Azure EA Enterprise Administrator role to assign permissions.
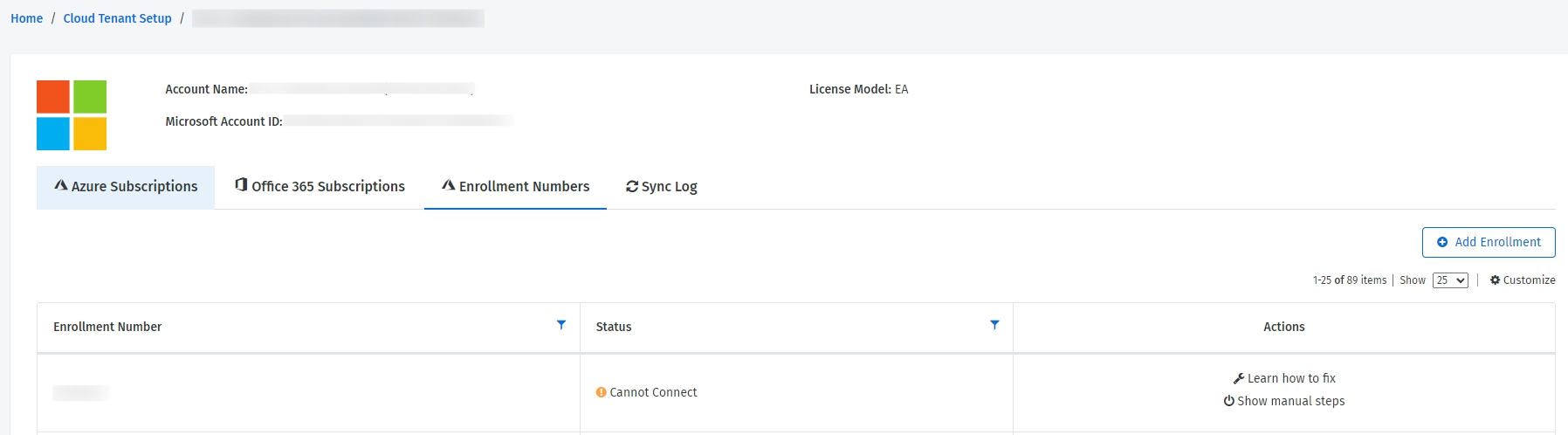
The Enrollment Numbers tab on the details page of the cloud tenant displays the enrollment numbers that are migrated to the new API, along with the respective enrollment status:
Connected - Indicates that the system is connected and working as expected.
Cannot Connect - Indicates that the Client Portal doesn't have access to the new Azure Cost Management API and the EnrollmentReader permission is missing. You can assign permissions using the Azure Cost Management API or Azure Cloud Shell.
Activation Required - Indicates that the Client Portal can access the enrollment data, but the cloud account has not been set up as an EA account type.
If you're adding a new EA cloud account to the Client Portal, you'll need to provide the enrollment number while adding the account. For information on how to add a new EA account, see Activate your cloud account.
Manage access to all subscriptions and management groups in your tenant.
As a Global Administrator, you can manage all Azure subscriptions and management groups in your tenant by elevating your access.
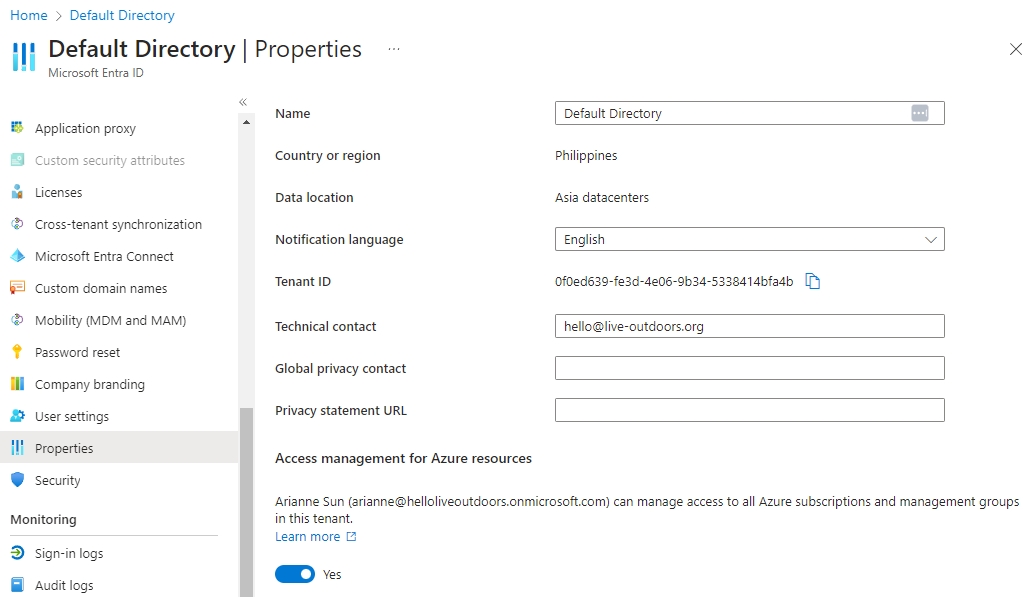
When you elevate your access, you'll be assigned the User Access Administrator role in Azure at root scope (/). This allows you to view all resources and assign access to any subscription or management group in the directory.
To elevate access, follow the instructions in Microsoft documentation: Elevate access to manage all Azure subscriptions and management groups, or perform these steps:
Sign in to Azure Portal as a Global Administrator.
Open Microsoft Entra ID. You can use the Azure search bar to find Microsoft Entra ID.
Under Manage, select Properties.
Under Access management for Azure resources, set the toggle to Yes.
This toggle is only available to users who are assigned the Global Administrator role in Microsoft Entra ID.
Click Save. This will grant you permission to assign roles in all Azure subscriptions and management groups associated with this Microsoft Entra ID.
If required, sign out and sign back in to refresh your permissions.
Elevate your permissions to manage all Azure subscriptions and management groups. See .