Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
You can access the Marketplace Platform from a browser on a Windows, macOS, or Linux computer.
We support the following browsers:
Google Chrome (latest version)
Microsoft Edge (Chromium) (latest version)
Mozilla Firefox (latest version)
Apple Safari for macOS (latest version)
If you don't use a supported browser, you might not be able to access the platform or use all of its features.
If you want to access the platform on a mobile device, ensure that your mobile browser meets the following minimum requirements:
The screen resolution must be at least 1024 x 768 (when browsers are maximized).
The cookies must be enabled.
JavaScript must be enabled.
We support the following mobile browsers:
Apple Safari for iOS (latest version)
Android browsers (the default browser on Android 13+)
When you terminate the last active subscription in an agreement or when subscriptions expire, the agreement status changes to Terminated. This termination is irreversible.
It means you can no longer use the terminated agreement for ordering new subscriptions and must either set up a new agreement when placing the order, or use an existing agreement in the Active state to attribute new subscriptions to that agreement.
See any of the related topic links for information on agreements and subscriptions.
The landscape of B2B subscriptions and procurement processes is undergoing significant changes as businesses transition towards subscription-based models. As a result, there is a need to navigate the complexities of managing orders and invoices in the context of subscription-based procurement.
This topic aims to answer your questions about B2B subscriptions while providing an overview of how subscription-based models differ from traditional procurement processes. It also describes how the Marketplace Platform makes it easier for you to manage and streamline subscription-based procurement.
In a subscription-based model, you pay a certain fee to access software or a service. You commit to a term and then pay a certain amount on a monthly or yearly basis.
This model differs significantly from the traditional purchasing model where you place a purchase order, the vendor processes it, and then issues an invoice after the license is allocated.
In traditional transactional procurement, the procurement process is linear, which means it involves placing a purchase order, processing of invoices, and reconciling them. In this model, each purchase order is directly linked to an invoice.
However, in a subscription-based model, the relationship between orders and invoices is complex. Unlike traditional procurement, where orders and invoices have a one-to-one relationship, in the subscription-based model, orders and invoices can have a many-to-many relationship.
For example, you might place multiple orders for additional licenses in a month, but receive only one invoice at the end of the month. Alternatively, you might not place any order, yet receive an invoice for subscription renewal. In these scenarios, orders don't directly match the invoices.
This causes an issue during reconciliation due to a mismatch between the number of orders and invoices.
Many enterprise procurement systems support subscription-based models through various mechanisms, such as recurring purchase orders, standing orders, blanket purchase orders, open purchase orders, contract management, and more.
Unlike traditional purchase orders, where each purchase order is linked to a single invoice, mechanisms (such as recurring purchase orders) represent long-term agreements, allowing multiple invoices to be associated with a single purchase order. This approach is useful in environments where regular, repeated purchases are common, such as in subscription-based billing systems.
To explain how our platform supports this process, it's important to understand the key elements of our platform.
The Marketplace Platform facilitates transactions between clients and vendors in various countries where SoftwareOne operates. We deal with objects such as orders, subscriptions, and agreements, which represent a relationship between the SoftwareOne entity and the client in specific regions.
Business transactions are represented by orders, which can be of different types, such as purchase orders, change orders, and termination orders.
Subscriptions are linked to agreements and represent the provision of service over a period of time. It's common for our clients to have multiple subscriptions within the same agreement.
To modify subscriptions, an order needs to be placed. It’s not possible to modify a subscription directly without placing an order.
Placing an order establishes a relationship at the recurring purchase order level on the procurement system's side and the agreement on the marketplace platform's side. This simplifies the reconciliation process when invoices are received because each invoice has links to the agreement, recurring purchase order, and subscriptions.
You can provide your recurring purchase order number in the Additional ID field when placing your order. This number will be used for reference in all consolidated invoices in the scope of each agreement in the platform.
After you've provided the number, it'll be displayed on the invoice as follows:
If a recurring purchase order number needs updating or changing during the subscription term, you can modify the Additional Agreement ID in the scope of the agreement. The updated number will then be reflected in your next invoice.
This option to update the PO number is available for the Adobe VIP Marketplace products only.
If you forget your password and can't sign in to the platform, you can reset your password using the Forgot password? link on the sign-in page.
You can also change your password through your profile page. To change your password, you must be signed in to the platform.
Follow these steps to reset your password:
On the Sign in page, enter your email address and select Continue.
Click Forgot password?.
In Forgot Your Password?, enter your email address and click Send Email. You'll receive an email containing a link to reset your password.
Click the link and follow the onscreen instructions to create a new password.
Follow these steps to change your password:
Sign in to your account.
Select your account menu and click My profile. Your profile page opens.
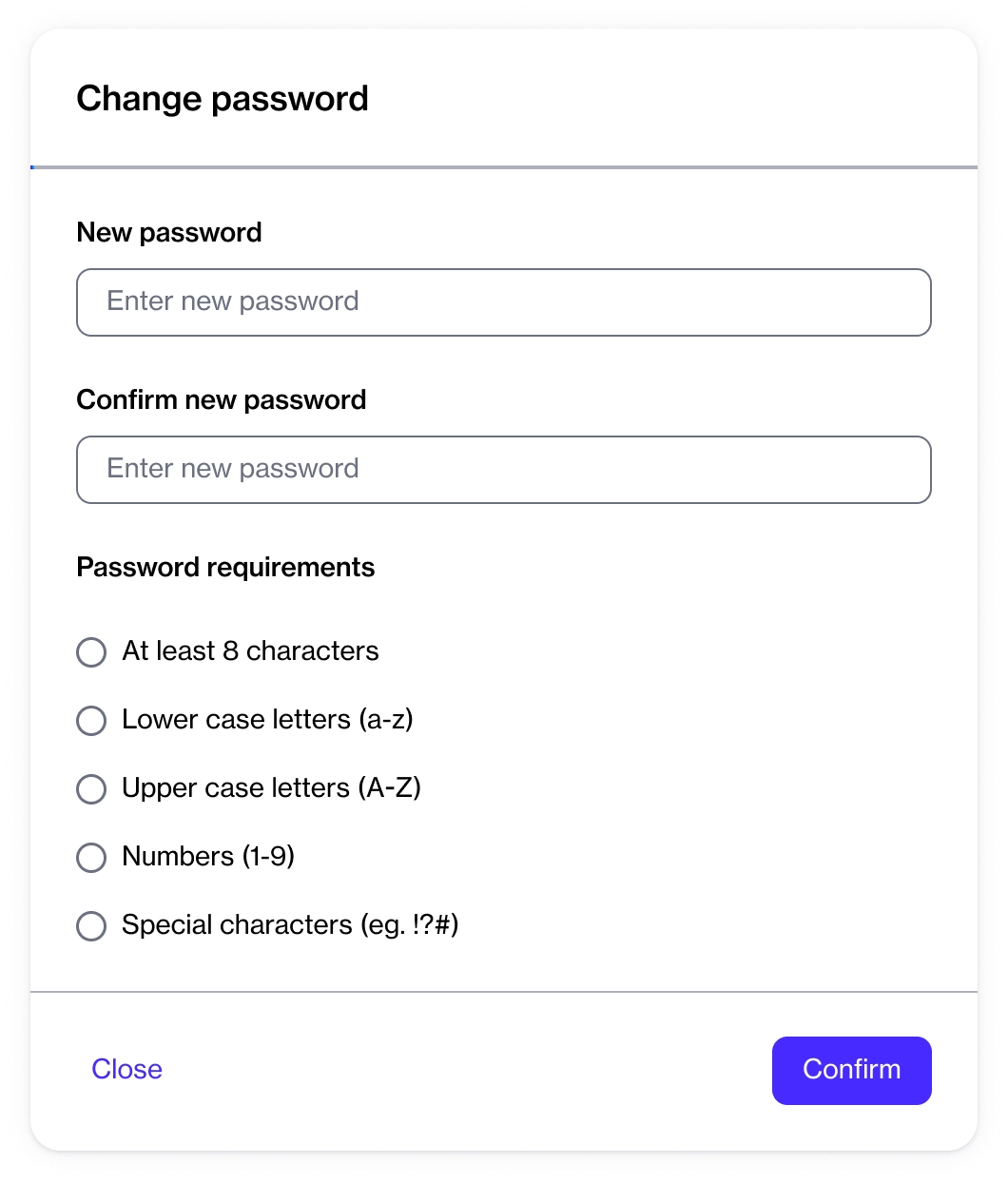
Click the chevron in the upper right and select Change password. The Change password page opens.
Enter your new password and then confirm that your new password matches the one you entered in Confirm new password. As you start typing your new password, our password validation checks whether your new password meets the requirements.
Click Confirm to save your changes.
This article explains how the platform connects to your Azure environment, how data is collected, and what security measures are in place.
An Access Token is used to enable the platform to collect spend details about your Azure Subscriptions. Without this Access Token, we are unable to pull this detail and provide you with the analytics necessary to make decisions about your day-to-day spending.
The customer must be assigned the “Owner” role in the Azure subscriptions you wish to add to the Client Portal.
When adding Azure subscriptions, the SoftwareOne service principal is granted “Tag Contributor” access to those subscriptions. This level of access allows full access to the Azure subscription without managing security settings.
The Client Portal uses this access to retrieve a list of your resources (Virtual machines etc.) and the tags assigned to them. This role also provides a level of access to synchronize any user-assigned tags in the Client Portal back to the resources of the Azure subscription. Azure built-on roles reference.
Tag Contributor lets you manage tags on entities, without providing access to the entities themselves. For more information, see the Microsoft documentation.
Being established as a 'Tag Contributor' allows the platform to interact with customers' spending and resource data. Without this, we are unable to provide custom reporting, and consumption views and successfully implement other workstreams within Spend Management.
When you perform consent, you are redirected to Microsoft to accept permissions required by the platform. As part of this process, the platform can “impersonate” the consenting user for a short period (1 hour).
The platform uses this impersonation to perform actions on behalf of the consenting user. This includes:
Assigning the Tag Contributor role to the platform for subscriptions owned by the consenting user during onboarding.
Assigning the Tag Contributor role to the platform for subscriptions owned by the consenting user during the addition of more subscriptions to the platform.
When the consent process is performed, a “service principal” is created in your tenant. This is conceptually similar to adding a user dedicated to the Client Portal for the purposes of accessing your tenant and subscriptions.
Yes, the platform offers application-level rights that you can change, after adding your Azure Subscriptions. Those include:
No Resources - No resources or tags will be synchronized from subscriptions marked with this setting.
No Tags – Your resources will be synchronized from your Azure Subscription, but their tags will not be synchronized in either direction.
Read Tags Only - Your resources will be synchronized from your Azure Subscription, including their Tags. Any changes to Tags in the platform will not be written back to Azure.
Read and Write Tags (Default Role) – Your resources will be synchronized from your Azure Subscription, including their Tags. Any tag changes in the platform will be written back to Azure.
When the Read/Write permissions are enabled, the platform can write into a customer environment. Write permissions are restricted to Tags only.
Role-based access control (RBAC) in the platform ensures that only a level of interaction that is acceptable to you is established between the platform and your cloud provider.
The platform makes extensive use of data encryption for data in transit:
Traffic from the platform is encrypted using HTTPS in their web browser.
API traffic between the platform and Microsoft’s services is all encrypted. Traffic is natively encrypted since it is an HTTPs request.
Partner Admin Link (PAL) enables Microsoft to identify and recognize SoftwareOne as helping customers achieve business objectives and realize value in the cloud. Customers must first provide partner access to their Azure resources. Once access is granted, the SoftwareOne Microsoft Partner ID (MPN ID) is associated.
The PAL association to existing credentials provides no new customer data to Microsoft or SoftwareOne. For more information, see the Microsoft documentation.
Find answers to some of the commonly asked questions.
Our platform has an SSO Authentication framework that integrates with existing Identity provider tools (such as Azure AD and ADFS) and SAML-based tools (such as Okta and Ping).
The customer provides SoftwareOne with basic metadata about their IdP. If your SSO tool requires the Assertion Consumer Service URL and Entity ID, please contact SoftwareOne.
SoftwareOne proceeds with a basic setup on the Client Portal IdP and provides the customer with {connection_name} that'll be used for further configuration.
The customer proceeds and finalizes the setup from their side.
All logins to the Client Portal for any of the specified IdP domains will be federated out to the customer's SAML-based IdP.
IdP Domains: List of email domains, for example @user.org, for which authentication should be federated out to the customer's IdP.
Sign In URL: HTTP-POST or HTTP-Redirect binding.
Sign Out URL
X509 Signing Certificate: In the .pem or .cer format.
We support the items listed in the following table:
Supported Protocol Bindings
HTTP-POST & HTTP-Redirect
SAML Authentication Requests signed
Yes (by default)
Sign Request Algorithm
RSA-SHA256 (default) or RSA-SHA1
Sign Request Algorithm Digest
SHA256 (default) or SHA1
Signing Certificate Strength
2048 Bit RSA
IdP-Initiated SSO
Supported, but strongly discouraged
{connection_name} is a verbatim string that SoftwareOne will provide after receiving the initial configuration settings from you.
Entity ID
urn:auth0:pyc:{connection_name}.
Example: If your connection_name is demo_company, the Entity ID on Production will be
urn:auth0:pyc:demo_company
Assertion Consumer Service URL
https://{idp_base_url}/login/callback?connection={connection_name}
Example: If your connection_name is demo_company, the Assertion Consumer Service URL on Production will be: https://login.pyracloud.com/login/callback?connection=demo_company
Metadata URL
https://login.pyracloud.com/samlp/metadata?connection={connection_name}
Single Logout URL
https://login.pyracloud.com/logout
Single Login URL
The Client Portal requires the following attributes via the specified mappings:
user_id
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier
Fallback URL 1: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn
Fallback URL 2: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
name
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
email
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress
given_name
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname
Fallback URL: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
family_name
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname
The attributes must satisfy at least one mapping for all properties above. If your IdP provides values for the required attributes in different claims/namespaces, please provide a list of claims to be used for all attributes above.
Please make sure to provide the attribute values as they are without any modifications.
URLs are sometimes changed by security software, for example, Proofpoint’s Targeted Attack Protection adds urldefense.com at the beginning of links.
To set up SSO with the Client Portal via Azure AD, you must complete the following steps. After you've completed these steps, SoftwareOne will enable SSO with your Azure AD.
Follow these steps to register the Client Portal as an application inside your Azure subscription:
Sign in to the Microsoft Azure Portal. If you have access to more than one tenant, select your account from the upper right corner. Set your portal session to the Azure AD tenant that you want.
Search for and select Azure Active Directory.
Under Manage, select App registrations.
Select New Registration.
In Register an application, enter a meaningful application name to display to the users, for example, Client Portal.
In Supported account types, select Accounts in any organizational directory (Any Microsoft Entra directory - Multitenant).
In Redirect URI, select the Redirect URI type as Web, and enter your callback URL: https://login.pyracloud.com/login/callback.
Click Register.
SoftwareOne will use the client secret to interact with your Azure subscription on behalf of the created application.
Follow these steps to create a secret:
From the Overview page of the app, select Certificates & secrets > Client secrets > New client secret.
Add a description for your client secret.
Set the expiration date for the secret.
Select Add.
Make a note of the client secret value. Note that the value will not be accessible again after you leave this page.
We recommend that you create a reminder to renew your client secret, at least two weeks before it expires. Once you've created a new secret, provide the value to SoftwareOne so that it can be updated in the system. If your client secret has expired or is no longer valid, you will be unable to sign in to the Client Portal using SSO.
Follow these steps to add permissions that allow read access to users and the user directory:
From the app Overview page, select API permissions.
Under Configured permissions, select Add a permission.
Configure permissions for the Microsoft Graph API.
Once you've selected the API, you'll see the Request API Permissions page.
Enable the following permissions:
Users > User.Read
Directory > Directory.Read.All
Select Add permissions to complete the process.
Enabling the Directory > Directory.Read.All permission is optional. If you want to benefit from future user auto-provisioning, then turn it on. However, for SSO to work, this permission is not required.
Provide the following information to SoftwareOne. Once received, SoftwareOne can complete the setup and the Client Portal will automatically start forwarding all users of the specified IdP domains to your Azure AD for federated authentication.
Application Client ID
Application Client Secret
Microsoft Azure AD Domain
Your Azure AD domain name. You can find this on your Azure AD directory's overview page in the Microsoft Azure portal.
IdP Domains
A list of all email domains that must be authenticated through the federated Azure AD, for example, @customer.com. Usually 1 domain but can also be multiple.
We support the items listed in the following table:
Identity API
Azure Active Directory (v1) (default) & Microsoft Identity Platform (v2).
Protocol used for federated Sign-In
OpenID Connect (default) or WS Federation.
Application type
Multitenant / Web
Redirect URI
https://{idp_base_url}/login/callback*
The redirect URI on Production will be:
https://login.pyracloud.com/login/callback
The Client Portal queries the following basic profile attributes from Azure AD:
upn
azure_id
given_name
family_name
nickname
tenantid
oid
name
The customer configures their ADFS server according to technical requirements.
The customer provides ADFS Metadata/IdP domains to SoftwareOne.
SoftwareOne will complete the ADFS setup.
ADFS Metadata Source
Either the URL or the Federation Metadata file. The URL usually ends in /FederationMetadata/2007-06/FederationMetadata.xml.
IdP Domains
List of all email domains that should be authenticated through the federated ADFS server, for example, @customer.com.
Usually 1 domain, but can also be multiple.
We support the items listed in the following table:
Federation Metadata Discovery (Automated Certificate Rollover)
Yes – if ADFS Metadata Source is provided as URL.
Realm Identifier
urn:auth0:{environment_name}
For example, urn:auth0:pyc on Production.
Endpoint
https://{idp_base_url}/login/callback*
The endpoint URL on Production will be: https://login.pyracloud.com/login/callback
By default, the Client Portal expects the following attributes from ADFS via the specified mappings:
E-Mail-Addresses
E-Mail Address
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress
Display-Name
Name
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
User-Principal-Name
Name ID
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier
Given-Name
Given Name
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname
Surname
Surname
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname
The customer provides Signing Certificates/IdP domains to SoftwareOne.
SoftwareOne will complete the SSO setup.
PingFederate Server URL.
X509 Signing Certificate in the .pem or .cer format.
IdP Domains: List of all email domains that should be authenticated through the federated ADFS server (for example, @customer.com). Usually just one, but can also be multiple.
Attribute Mappings
By default, the Client Portal requires the following attributes via the specified mappings:
user_id
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier
Fallback URL 1: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn
Fallback URL 2: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
name
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress
given_name
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname
Fallback URL:
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
family_name
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname
The provided attributes must satisfy at least one mapping for all properties above. If your IdP provides values for the required attributes in different claims/namespaces, please provide a list of claims to be used for all attributes above.
If an email domain is federated out to the user's identity provider, it's possible that the Client Portal will receive sign-in attempts from users who are not set up as Client Portal users.
In such cases, if authenticated users from a federated connection are not Client Portal users, their login to Client Portal will fail with an error message stating that their account is not set up and they don't have access.
In some cases, the consumption data for your Azure Reserved Instances might be unavailable in the Client Portal.
If you are not able to view the data, you must update your permissions and assign the Reservations reader role to each tenant through the Azure Portal.
To learn about the Reservation reader role and how to assign it, see . You can also assign the role by following the steps in this topic.
You can assign the Reservations reader role only if you have the User Access Administrator or Owner role in Azure. If you need to elevate your access, see .
Follow these steps to assign the role:
Sign in to the and search for Reservations.
Select Role Assignment.
On the Access Control page, click Add > Add role assignment. The Add role assignment page opens.
On the Role tab, select Reservations Reader as the role and click Next.
On the Members tab, do the following:
Select User, group, or service principal if it's not selected by default, and then click Select members.
In the Select members panel, type PyraCloud and then select PyraCloud (Azure) from the search results.
Click Select.
Click Review + assign.
On the Review + assign tab, review the details and click Review + assign to confirm the role assignment.
After you've completed these steps, the Reservations Reader role is assigned and displayed on the Role assignments tab.
The Client Portal downloads AWS recommendations from and .
If the Client Portal is unable to download recommendations, a message is displayed in the health check for the AWS accounts on the Cloud Cost Optimization page.
The following image shows the AWS synchronization error:
This error means that the AWS Trusted Advisor or Cost Explorer is not configured correctly for at least one AWS account.
To resolve this issue:
Select Fix.
On the Synchronization Information page, review the details and follow the solution to resolve the error.
The following are the possible issues and their description:
Microsoft has released a preview feature to support allowing access to service providers (like SoftwareOne) through Conditional Access policies. To learn about Conditional Access, see the .
To exclude SoftwareOne and the Client Portal from your blocking Conditional Access policies, you'll need the Microsoft Tenant IDs of SoftwareOne’s reseller tenants that relate to you.
Even though SoftwareOne has over one hundred of these reseller tenants, only one or two will apply to you. The only way to find out the reseller tenant IDs you need to use is to log a support ticket with our Support team.
For configuring conditional access policies, determine which Conditional Access policies are blocking SoftwareOne and the Client Portal.
Before you can exclude Client Portal and SoftwareOne from your policies, you need to know exactly which policies are affecting access. You can do this using the What If capability of Conditional Access.
Follow these steps to configure conditional access policies
In the Azure portal, navigate to .
Select What If in the top navigation bar.
On the What If page, select No user or service principal selected and then choose the following settings:
Select identity type: User
Select: Guest or external users
Select: Service provider users (preview)
Select organization (preview)
Click No Tenant selected.
Enter the Tenant ID you obtained from our Support team.
Click the tenant that is found.
Click Select.
Select What If.
At the bottom of the page, you will see the list of Policies that will apply. Make a note of these policies as these are the ones you will need to modify to exclude the Client Portal and SoftwareOne.
When modifying Conditional Access policy exclusions, do not remove any of your existing excluded users, groups, or other principals. With Conditional Access, there is a very real possibility of locking yourself out of your tenant. Only attempt the following steps if you are a Conditional Access expert and you are confident configuring them.
SoftwareOne cannot be held liable for damages caused by the misconfiguration of this feature.
In the list of policies, select one of the policies that you applied.
Under Assignments, select the Users section.
Select Exclude.
Select the Guest or external users checkbox.
Choose Select.
Click 0 Azure AD organizations selected.
Enter the Tenant ID you obtained from our Support team, and then select the checkbox next to the SoftwareONE reseller tenant.
Click Select and then select Save.
Repeat the steps in this section for each policy that you noted in the previous section.
At this point, you may wish to temporarily change the policy to Report-only to check whether existing access is still working correctly. If you do this, please remember to enable the policy again once you are confident it is working as expected.
365 Analytics reporting uses application consent to collect data from your Office 365 tenant. Application consent is used to collect data via the Graph API.
To learn why this is important, what data is collected, and what security measures are in place,
Follow these steps to connect your 365 tenant:
Browse to the URL that SoftwareOne provided. You'll either receive the URL from the SoftwareOne support team or you'll see a banner in 365 Analytics stating that the data collector requires additional permissions.
Sign in to PyraCloud with the agreed global administrator account. Use the password that was set in PyraCloud, not your Office 365 account password.
Select Connect Tenant.
Enter your Office 365 Tenant ID.
Enter your Office 365 global administrator account username and password. Use your Office 365 Azure AD account, not your PyraCloud credentials. The user must be a Global Admin for authorization to work.
Authorize 365 Analytics access to read your Office 365 Tenant. Select Accept.
Notify your SoftwareOne representative.
We strongly discourage using IdP-Initiated SSO flows because they are vulnerable to . If possible, let the Client Portal initiate the sign-in (and federate out) when required.
You can find the Application (client) ID on the overview page of the application created in .
Your client secret as created in .
Once the role is assigned, it might take up to 24 hours for your consumption data to become available in the Client Portal. If you are not able to view the data after 24 hours, .
If you've enabled the Cost Explorer and AWS permissions, but the Client Portal is still showing an error, ensure that the Amazon EC2 rightsizing recommendations are enabled. For information on how to enable rightsizing recommendations, see in AWS documentation.
In the Azure portal, navigate to .
Cannot read recommendations from AWS Trusted Advisor
It means that the Client Portal doesn't have the right permission to pull data from AWS Trusted Advisor.
Cannot read recommendations from AWS Cost Explorer
It means that Client Portal doesn't have the right permission to pull data from AWS Cost Explorer.
Cannot read recommendations from AWS Trusted Advisor due to support plan
It means that the AWS account has low support to download data through API for Trusted Advisor.
AWS Cost Explorer disabled in the Client Portal
It means that the synchronization of recommendations from AWS Cost Explorer is not enabled in the Client Portal.
AWS Cost Explorer disabled in AWS
It means that AWS Cost Explorer is not enabled in the AWS account.
The platform uses several Microsoft APIs to pull data that allows you to create Spend reports, Budgets, and Chargebacks. In some cases, it can take up to 24 hours for the resource cost to be accessed through the interface.
As the platform synchronizes your Azure billing data only once a day, sometimes, it might take 48 hours for the data to refresh.
Additionally, the reconciliation files are available no later than the 8th day of every month. Microsoft invoices partners based on this file. Therefore, we recommend that you send chargebacks after the 8th day of the month.
For more information, see Reconciliation file availability and Microsoft Partner Center data delay.
Microsoft offers two primary API sets for accessing M365 services called PowerShell and Microsoft Graph.
PowerShell access requires the 365 Analytics application to authenticate to the service using a named credential instead of the enterprise application registration. That’s where the service accounts come in. 365 Analytics supports Reporting Service Accounts.
Graph API access is managed through the Azure AD enterprise applications deployed as part of 365 Analytics provisioning in a tenant.
The Reporting Service Account is used to gather data from the target tenant using both PowerShell and Microsoft Graph. It is a read-only account and is required for all tenants. We recommend and have tested assigning the Global Administrator role to this account.
To learn about creating service accounts for 365 Analytics reporting, see How to create service accounts for 365 Analytics reporting.
365 Analytics makes extensive use of data encryption for data in transit and at rest:
Traffic from 365 Analytics users is encrypted using HTTPS in their web browser.
API traffic between the 365 Analytics application and Microsoft’s services is all encrypted. Graph traffic is natively encrypted since it’s just HTTP requests; other protocols, such as remote PowerShell, are tunneled over HTTPS.
All 365 Analytics data is encrypted at rest.
All service account credentials held by 365 Analytics for reporting are stored and encrypted in two places:
The Service Account password is encrypted before it leaves the client machine setting the password; whether that is via the User Interface or PowerShell script. It is therefore sent in an encrypted form to our backend servers. Only our job collection servers have the private key to decrypt this password.
The encrypted service account password is then further protected by being stored in Azure Key Vaults, where only our ‘job engines’ (those services that collect data) have access to the key vault to obtain the data.
As of May 2020, Microsoft does not support the use of multi-factor authentication (MFA) for accounts used as service accounts in Office 365. This is not a 365 Analytics limitation, it’s a restriction imposed by Microsoft.
The default policies applied by the service will break 365 Analytics service account access because they require MFA for accounts that hold the Global administrator role.
Microsoft’s recommended solution is to enable conditional access whitelisting for the IP addresses used to access M365 services using these service accounts.
NOTE: The default conditional access policies available to all Office 365 customers do not support whitelisting; customers who do not currently have O365 licenses with support for the full set of conditional access features may need to purchase additional licenses from Microsoft.
If you require a list of IP addresses used for the reporting service account, contact marketplace-support@softwareone.com.
An access token may be invalid due to the following reasons:
The token is incomplete: If your access token is incomplete, sign in to the Azure Portal and copy your access token again.
The token is complete but has expired: If your access token has expired, you must generate a new token.
The token is complete but has been revoked: If your access token has been revoked, you must generate a new token.
When you perform consent, you are redirected to Microsoft to accept permissions required by the Client Portal. As part of this process, the Client Portal is able to “impersonate” the consenting user for a short period (1 hour).
The Client Portal uses this impersonation to perform actions on behalf of the consenting user. This includes:
Assigning the Reader role to the Client Portal for subscriptions owned by the consenting user during onboarding.
Assigning the Reader role to the Client Portal for subscriptions owned by the consenting user during the addition of more subscriptions to the Client Portal. For more information, see Adding more subscriptions.
Modify the default Reader role to the Tag Contributor role (and vice versa) during the Change Access process. For more information, see Sync your tags to Azure.
When the consent process is performed, a “service principal” is created in your tenant. This is conceptually similar to adding a user dedicated to the Client Portal for accessing your tenant and subscriptions.
When adding Azure subscriptions, the service principal is granted “Reader” access to those subscriptions. This is a built-in role in your Microsoft tenant that allows read-only access to your resources. The Client Portal uses this access to retrieve a list of your resources (virtual machines, websites) and the tags assigned to them.
If you change the level of access to a setting that allows the write-back of tags, the Client Portal requires the “Tag Contributor” role. This level of access allows full access to your subscription with the notable exception of managing security settings in the subscription. The Client Portal uses this access to retrieve a list of your resources (virtual machines, websites, etc.) and the tags assigned to them. It also requires this level of access to synchronize the tags you assign in the Client Portal back to the resources of your Azure subscription.
For more information, see Microsoft documentation - Azure built-on roles reference.
When adding Office 365 subscriptions, the service principal is granted permission to the Microsoft Graph API in your Microsoft tenant. Those permissions include:
Read all usage reports: Allows an app to read all service usage reports without a signed-in user. Services that provide usage reports include Office 365 and Azure Active Directory.
Read all groups: Allows the app to read memberships for all groups without a signed-in user. Note that not all group API supports access using app-only permissions.
Read all users’ full profiles: Allows the app to read the full set of profile properties, group membership, reports, and managers of other users in your organization, without a signed-in user.
For more information, see the Microsoft Graph API permissions reference.
If your report is empty and you receive this message There is no data for this chart, there are a few reasons for this, including:
The data is being filtered in a way that no data is returning. You might need to edit your report and modify the filters.
The data might require access to the Security and Audit Logs that may not have been configured. Check your 365 Analytics settings.
The data has not been collected as the data collection needs to be authorized.
You may need to reauthorize your tenant. For information, see How to connect your 365 Tenant for data collection.
If you've completed these steps and still have the notification or the report is empty, contact our Support team.
365 Analytics Reporting uses a service account to collect data from O365 tenants. Service accounts are used to collect data via PowerShell in cases where data can’t be collected via GraphAPI. You can create service accounts using PowerShell and Microsoft 365 Admin Center.
Your organization will not be charged by Microsoft for this account as it does not require an Office 365 license.
We recommend that you use PowerShell to create service accounts because this method contains fewer steps.
Before creating an account, make sure that you're connected to Office 365. If you are not, then follow these steps to connect to Office 365:
Install the Microsoft Online Service Module on your system.
Open Windows PowerShell and copy and paste the following commands:
When prompted, enter the username and password of the Office 365 Administrator account. Your account will be connected to Office 365 in PowerShell.
Follow these steps to create a service account:
After your account is connected to Office 365 in PowerShell, follow these steps to create a service account:
Modify the following line and set company.onmicrosoft.com to match your own Office 365 .onmicrosoft.com domain.
Replace the password with a secure password. We recommend a password of 10 characters or more and including capital and lowercase letters, numbers, and special characters.
Add the new account to the ‘Global reader’. You can do this by copying and pasting the following line into the PowerShell window.
Check if the service account was set correctly by running the following PowerShell commands:
You'll not receive a confirmation if the commands are successful.
You can create a service account via the Microsoft 365 Admin Center, however, you'll still need to run a final PowerShell cmdlet to ensure that the password doesn't expire.
To create a Service Account using the Microsoft 365 Admin Center
On the Admin home page, go to Users > Active users and select Add a user.
Enter the display name as Service Account for 365 Analytics and the user name as 365Analytics.
Ensure that the domain is the company.onmicrosoft.com.
Select Let me create a password and enter the new password.
Ensure that the Require this user to change their password when they first sign-in option is not selected.
In the Product Licenses page, choose Create user without product license.
In the Optional settings page, choose Admin Center access and select Global Reader.
Review the data and select Finish adding on the last page.
If the password of the service account has expired or needs to be changed, you must change it in Office and in the Tenant Management System Client.
If your company policy allows passwords to never expire, you can do so using the following PowerShell command:
365 Analytics requires a Microsoft Application consent. 365 Analytics Reporting uses application consent to collect data from your Office 365 tenant. Application consent is used to collect data via Graph API.
For information on how to authorize the 365 Analytics Application for read-only access to your Office 365 tenant, see How to connect your 365 tenant for data collection.
The platform imports information from your Microsoft 365 tenant daily. The data is used in the following features:
Tag & Resource Manager - Used to allocate resource costs to business units (custom groups), Tag & Resource Manager (TRM) imports information about Azure AD user accounts including (but not limited to) usernames, display names, departments, managers, addresses, and extensionAttributes. This information is used to help the user allocate license costs to the correct business unit. TRM also imports information about specific Microsoft 365 licenses assigned to users.
Consumption - Used to report on resource usage and cost, Consumption imports information about overall Microsoft 365 license quantities and assignments. This includes total purchased licenses, total assigned licenses, and total unassigned licenses for each subscription.
The Marketplace platform does not access a customer's tenant on an ad-hoc basis for any reason related to Microsoft 365.
The platform uses an account called mfa.setup to access the Partner Center API for CSP customers. In some instances, the platform also 'double hops' into a customer's Microsoft tenant to get information about users and license assignments.
This account is used to access the Microsoft Graph API, specifically, the users and SubscribedSkus endpoints that provide the Client Portal with information about Azure AD users. It also provides information such as, how many licenses from each Microsoft 365 subscription are assigned and how many are free. To learn more about these APIs, see the Microsoft documentation on List users and List subscribedSkus.
To authenticate and consume these APIs, the platform uses app+user authentication. It means that when the platform authenticates, it uses a combination of both an Enterprise Application and a User Account (which is a service account, the aforementioned mfa.setup user).
For CSP, both these principles exist in SoftwareOne's Azure AD rather than in the customer's Microsoft tenant. For more information, see the Microsoft documentation on App+User Authentication.
Note that even under the new secure application model, app+user authentication is still used.
Unless configured, the Conditional Access policies (CAP) don't block authentication attempts by the enterprise applications. On the other hand, user account access can be actively blocked by CAP unless an exception is configured.
Historically, it has been challenging to configure exceptions for the user accounts in partner (SoftwareOne's) Microsoft tenants because they don't exist in the customer's Microsoft tenant.
Recently, Microsoft has added functionality to CAP to allow narrow (least privilege) exceptions to be configured for partner Microsoft tenants. For information, see How to Configure Conditional Access Policies and Conditional Access for External Users (Microsoft documentation).
The following fields are downloaded for each user in the customer's Azure AD and Microsoft 365 subscriptions.
These fields are not customizable in the platform. They must all be downloaded.
DisplayName
SkuId
CompanyName
SkuPartNumber
Department
SkuPrepaidUnits (Total purchased licenses)
SkuConsumedUnits (Total assigned licenses)
GivenName
SkuServicePlans (Products associated with the subscription, for example, Office 365 includes Teams and Yammer, etc.)
Surname
JobTitle
State
PostalCode
StreetAddress
City
PreferredLanguage
UsageLocation
AssignedLicenses
UserPrincipalName
OfficeLocation
OnPremisesExtensionAttributes
Country
State
UserType
Delegation and Policy Control allows a variety of user types to do their jobs more productively, in a secure fashion, and without requiring elevated administration credentials.
Delegation and Policy Control (DPC) for Office 365 helps organizations become more productive by enabling granular roles and responsibilities to be assigned to selected users, such as help desk operators, country-level administrators, or even end-users, setting clear boundaries on all delegated permissions.
Providing more granular delegation than the default Microsoft administrator roles is especially important for larger enterprises, companies that have multiple operating entities or business units, universities, and any organization that needs to delegate access widely across the organization.
Delegation and Policy Control allow a variety of user types to do their jobs more productively, in a secure fashion, and without requiring elevated administration credentials:
Helpdesk teams are able to support users by setting passwords, resetting MFAs, adding a user to a group, enabling access to mailboxes, or creating new mailbox aliases
Business unit owners or procurement can assign licenses to people in their part of the organization
Business owners can manage their own teams whilst ensuring that naming conventions are adhered to
Office managers can set out-of-the-office notifications for users within a specific geography or business unit
HR personnel can correct data for users in AD or AAD and create mailbox aliases or set forwarding.
Without a toolset such as 365 Analytics DPC, Office 365 delegated administration is difficult to achieve as there are limited native capabilities for delegating administrative tasks. Many organizations solve this by increasing the number of Global Administrators (GAs), even though this is known to substantially increase security risks.
365 Analytics DPC resolves this dilemma by ensuring designated administrators can see and act on only the users that they are responsible for in a fashion that aligns precisely with their defined administrative role. This enables administrative tasks to be conducted where they are most effective and increases the productivity of the organization.
Having a member of the HR team raise a ticket to change an incorrect detail in AD, or an office manager raise a ticket to set an OOO notification for a user who has departed for vacation without doing so are both examples of how both help desk teams and business users’ productivity can be impacted by the absence of effective delegation.
DPC also provides a Virtual Organizational Unit (OU) which provides a way to group users, teams, or other elements into logical units which can then again be used to delegate rights to those who need to operate on these groups or teams.
All DPC actions are recorded in a 365 Analytics read-only log file, which enables the organization to track which actions were taken, by whom, and at what time.
Authorization policies allow a delegated administrator to perform a predefined action against a specific set of users. The actions defined in the authorization policy provide the ability to granularly restrict what the delegated admin can see or do.
The policy applies to objects such as Office 365 or on-premise users, a Teams team, or a Mailbox. Over 100 actions can be taken, such as setting a password, creating a Teams channel, adding a user to an AD group, or setting an OOO notification.
License Policies enable organizations to delegate the function of assigning O365 licenses. As an example, a delegated license administrator can be given a quota of licenses that are both E3 and E5 with a quantity of PowerBI and Visio.
The E3 licenses may be restricted to only Exchange, OneDrive, SharePoint, and Teams. The E5 licenses could be unrestricted. When a request is made for a license, the delegated license administrator would assign the appropriate license and that would be removed from their quota.
Configuration policies apply rules to users in a Virtual OU. For example, to ensure that all users have MFA enabled, have a specific Microsoft usage location, or assign a specific license type. This ensures the configuration for users, groups, and other AD objects is correctly configured according to what has been determined appropriate for that group of users.
Configuration Policies ensure standard configurations are applied to particular groups or departments by standardizing objects wherever the policy is applied. For example, if you have a virtual organizational unit for the Sales department, all users in this container will have their Department attribute equal to ‘Sales’. Once a user is moved into this container, he or she will be brought into compliance with the configuration policy for Sales.