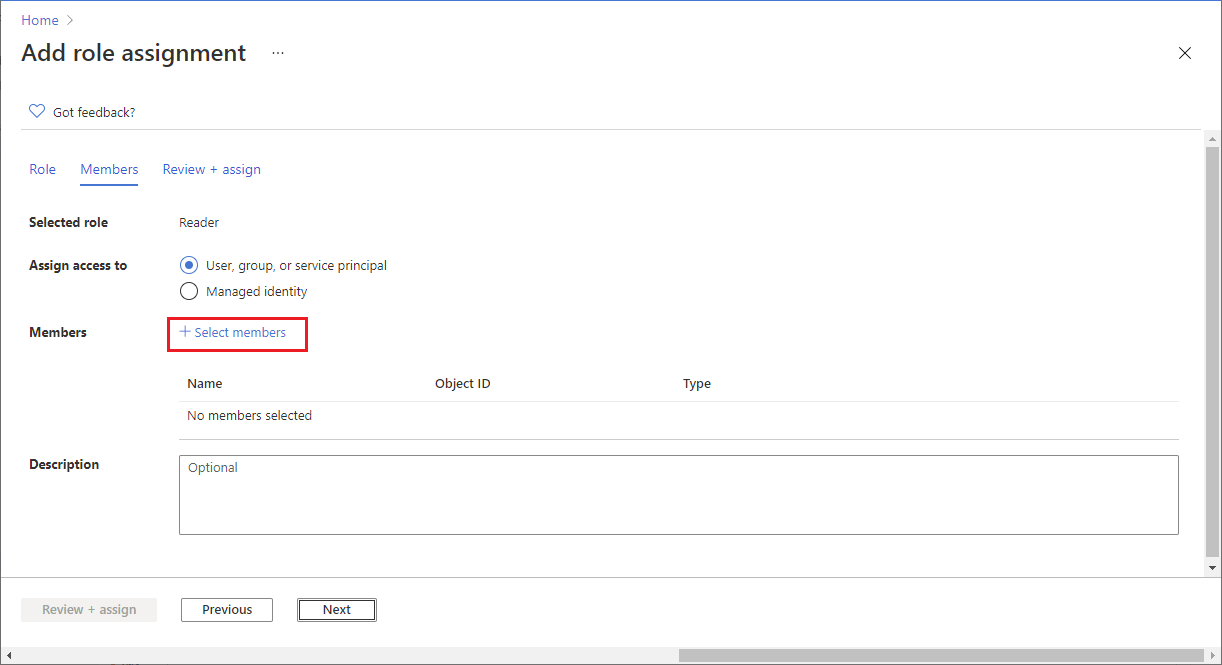
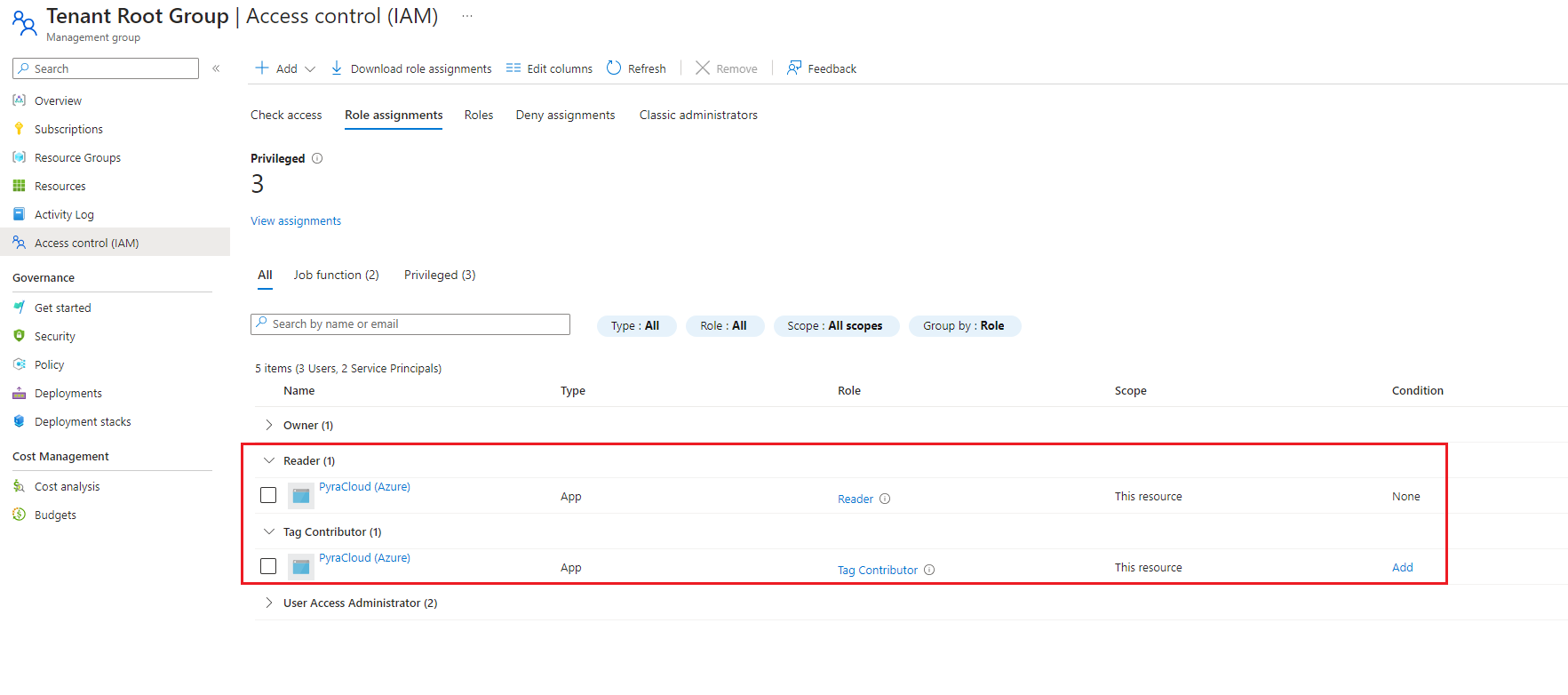
Assign Reader and Tag Contributor Roles (multiple subscriptions)
Granting access using Azure CLI
az login
az rest --method post --url "/providers/Microsoft.Authorization/elevateAccess?api-version=2016-07-01"
az ad sp create --id 2a4807a4-d9e4-457d-b32f-a455e0d3662a
az ad app permission grant --id 2a4807a4-d9e4-457d-b32f-a455e0d3662a --api 00000003-0000-0000-c000-000000000000 --scope "User.Read"
$root_mg=$(az account management-group list --query "[?displayName == 'Tenant Root Group'] | [0] | id" --output tsv)
az role assignment create --assignee "2a4807a4-d9e4-457d-b32f-a455e0d3662a" --role "Reader" --scope "$root_mg"
az role assignment create --assignee "2a4807a4-d9e4-457d-b32f-a455e0d3662a" --role "Tag Contributor" --scope "$root_mg"Command
Description
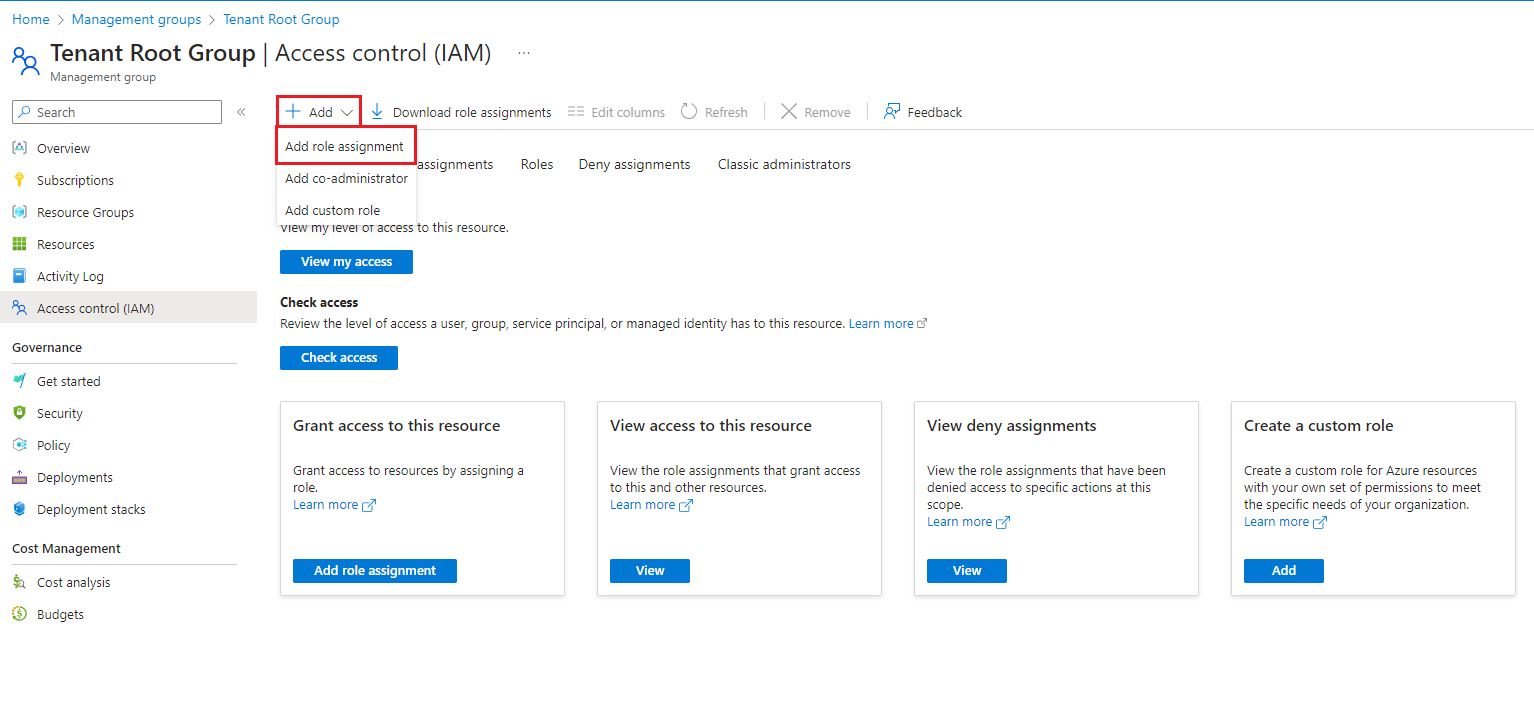
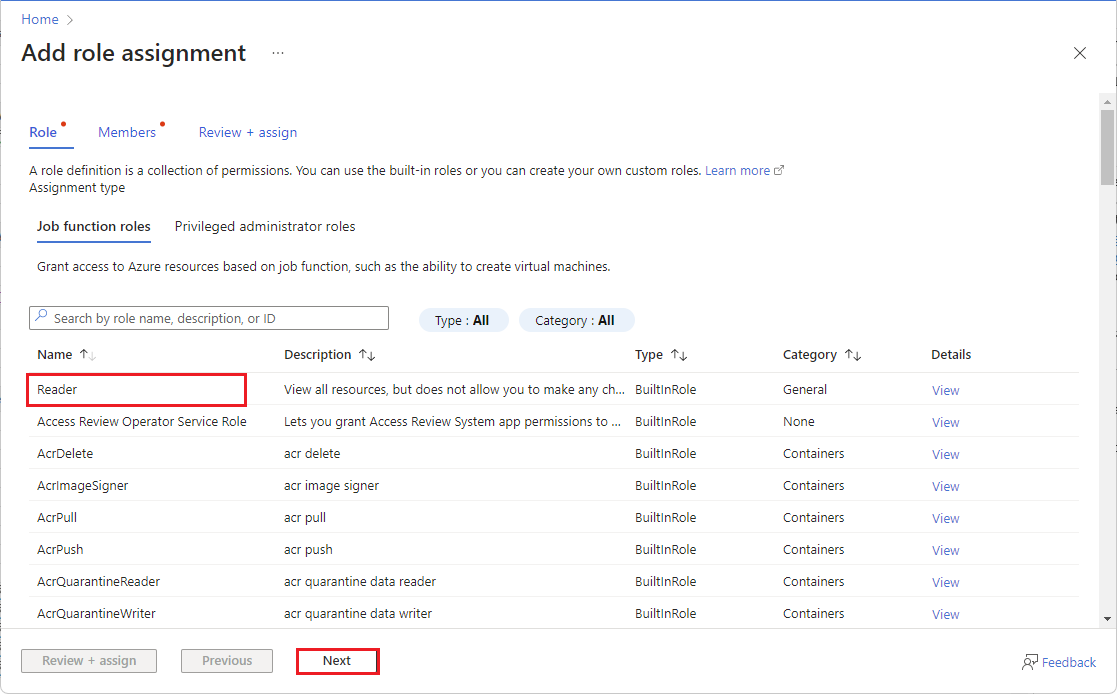
Granting access using the Azure Portal
PreviousAssign Reader and Tag Contributor Roles (single subscription)NextMigrate to Azure Cost Management APIs
Last updated
Was this helpful?